Reference no: EM13732964
Question: Implementation of sliding window protocol on a 6 node network. Specifications are given in the attached file.
Modules 1: Implementing Sliding Window Protocols using CNET
In this module, you are required to implement the "Sliding Window" protocol on a 6- node network. The topology of the network is given in Figure 1.
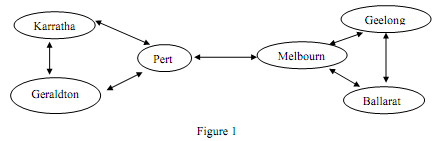
It is assumed that the nodes will communicate directly with each other if they are directly connected, otherwise the intermediate nodes will be used to relay the communications. No dynamic routing is required.
Please study the "stopandwait" sample files provided carefully, and build your work based on it. Your implementation should provide a mechanism for the nodes to address one another, and a service for the application layer to send message to a given destination address. Feel free to set the sizes of the sliding windows in each node as you wish and it is fine if you set them all to be the same. However please note that you need to demonstrate the cases when the window is exhausted, so do not set the window size to be too big. In the display window of every node, it is required to display the source and destination of each frame (which can be either a data or acknowledgement frame), while the sequence number are required on every data/acknowledgement frames.
Please note that you are NOT required to position the 6 nodes in geographically correct positions, i.e. we are interested in topology, NOT topography.
Write a short document (no more than 5 pages single space) describing your implementation of the "Sliding Window" protocol on the 6-node network. You need to describe the organization of your source code, and your implementations on some design issues such as sending, receiving, and re-transmission.
|
Environmental factors and organizational process assets
: The most important inputs for Risk Management Planning include: Environmental factors, organizational process assets, scope statement, and project management plan.
|
|
Role of ethics and social responsibility
: Explain the role of ethics and social responsibility in developing a strategic plan while considering stakeholder needs and agendas.
|
|
Write an essay on the progressive movement
: The History of Reconstruction, The Industrial Revolution, The Progressive Movement, America's Age of Imperialism, Final Paper Preparation, Women's Rights and Final Paper Preparation, Native Americans.
|
|
What is process modeling
: What is Process modeling? What is data-flow diagram? Why do systems analysts use DFD
|
|
Implementing sliding window protocols using cnet
: Implementing Sliding Window Protocols using CNET - It is assumed that the nodes will communicate directly with each other if they are directly connected, otherwise the intermediate nodes will be used to relay the communications. No dynamic routing ..
|
|
The four strategic choices for mnes
: Which of the following is NOT one of the four strategic choices for MNEs
|
|
Purchasing the brand products
: What are 2 demographic and 2 psychographic characteristics of the customer who you think would be interested in purchasing the brand's products?
|
|
What were the main causes of the reign of terror
: What were the main causes of the ‘Reign of Terror? Write a one paragraph obituary for someone who died during the Reign of Terror. Be creative!
|
|
Choose a topic in health care
: As your final task (Key Assignment), you will choose a topic in health care (e.g. cardiovascular issues, obesity, or cancer) and analyze it. Then, integrate all of the steps and standards that are needed to meet the quality improvement and perform..
|