Reference no: EM133340
CASE STUDY
The IP Version we are all using nowadays, in our corporate networks and in the Internet, is IP Version 4, short IPv4. It has been expanded in the early seventies by a number of pioneers who wanted to unite some educational and government networks in the United States. At the time when they started development, a network like our Internet nowadays was beyond imagination and consequently to meet such a condition wasn't part of their design goals. All the more fascinating it is, that they managed to create a networking protocol, which is still - 30 years later - competent of running today's Internet! But now it has reached it's age and can't be pushed any further. Instance for the next generation to take over!
When the Internet was switched overnight to use TCP/IP instead of the formerly used NCP in 1983, IPv4 was not precisely the protocol we know today. It was, in the core. But many of the additional rooms and additions that we use today have been developed much later. The essentials of IPv4 were defined in RFC (Request for Comment) 791 in 1981. Path MTU Discovery was defined in RFC 1191 in 1990, Super netting, which was designed to help ease the issue with loaded routing tables, was defined in RFC 1338 in 1992, DHCP, which was designed to help manage the addresses in a larger IP network, was classified in RFC 1531 in 1993 and Private Addresses which we use to build our NATs (Network Address Translation) today were labelled in RFC 1597 in 1994.
The motive I am mentioning this, is not to bore you with numbers of papers that you never want to read. What I would like to point out is that when IPv4 was first introduced, it was not the mature protocol we know today. Many of the extensions to IPv4 that help us manage and uphold our IPv4 networks were introduced later, when the requirement arose. Based on the need, the extensions were defined in the international working clusters and defined as RFCs.
So when individuals argue these days, that IPv6 is not mature and cannot do what IPv4 can, this is only partially true and above all, not a reason to not use IPv6. Development for IPv6 started in 1991. The core of IPv6 was standardized in 1995 and updated in RFC 2460 in 1998. Pedestal on that standard we have many implementations around since many years. Most hardware and router vendors have implementations since the late nineties and have tested them intensely. 6to4, a main transition mechanism, that makes co-existence and migration much easier, has been homogenized in 2001. DHCP Version 6 has been harmonized in summer 2003. Mobile IPv6, which is going to be one of the technologies that make you choose IPv6 over IPv4, is in the process of being standardized in early 2004. The same is true for ISATAP, another instance for a transition mechanism.
IPv6 has been expanded based on the rich experience we have with IPv4. IPv6 is an evolution of IPv4, it is mature in the core, it has been implemented and tested powerfully up to the network layer. The developers created a protocol, which takes the whole thing that was great about IPv4 and added flexibility to extend it, to make it the network protocol of the future. IPv6 is competent of handling the Internet growth rate and to hold up the new types of services, especially in the area of mobility that we have to wait for in the coming years.
There are obsessions that we are missing in IPv6 today that is true. But you do not need to switch today and all these additions will be defined in the coming years, just as it occurred with IPv4. But you ought to become aware of how IPv6 will impact your business and your network. If you plan early, you will save money and headaches. You will be ready when it is time for you and more importantly, you will be capable to determine the right instant for not extending your IPv4 infrastructure anymore, but putting your investments into the future technology.
Source : www.sunny.ch Author : Silvia Hagen Company: Sunny Connection AG, Staubergasse 9, 8124 Maur / Switzerland
QUESTION 1
a) A lot of practical problems have arise with the implementation of applications in IPV4 protocol. hardly any of them are:
i. Deploying Voice over IP
ii. Remote Management of Applications and Servers
iii. VPN between Same Address Space
iv. Address Plans and Secondary Addresses
Put in plain words the above with the necessary diagram where applicable
b) "All the more fascinating it is, that they managed to create a networking protocol, which is still - 30 years later - capable of running today's Internet! But now it has reached it's age and can't be pushed any further. Time for the next age band to take over!".
What are the two main motives for the above statement?
c) 10.1.0.3 is my IPV4 ip address.
i. Can you fit in this lecture to in an IPV6 address format?
ii. How will it appear like after embedding the above V4 address?
iii. What is the utmost bits a group of four decimal values hold in an IPV6 address? You are required to show your computation
QUESTION 2
a) i. You are employed as a safety network analyst in SAI Ltd. In SAI Ltd many of the network assets are not secured at all. After an audit in the company you noticed that the subsequent were in secure:
- Internet connections
- Public servers and e-commerce servers
- Remote access networks and VPNs
- Securing User Services
How would you secure the above?
ii. "Can you please correct the figure below, if you believe there is an error in the safekeeping design", instructed the network manager of SAI LTD.
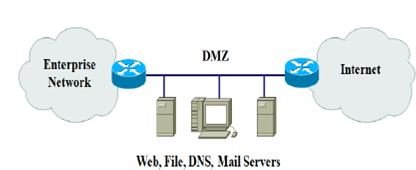
QUESTION 3
According to the layered-safekeeping approach there are safekeeping measures and modus operandi at five different levels within your IT environment.
I. Name the five dissimilar levels
II. Describe the primary three levels in detail.
QUESTION 4
HANGZHOU, April 19 (Xinhua) -- Chinese e-commerce giant Alibaba Group proclaimed Monday that one of its websites was hacked on Friday and Saturday and the police force were investigating.
Servers of Alibaba's foreign wholesale market, Aliexpress, in Hangzhou, east China's Zhejiang Province, and in the United States were hacked constantly on April 16 and 17, said Wu Hao, head of public relations at Alibaba Group.
The website, still in the checking phase, hosted the sale of Chinese goods in bulk to American buyers, said Wu.
"Our clients' information was not revealed or stolen. But some users could not access our website at some point," said Wu.
The company did not say where the attacks originated, but Wu told Xinhua that they considered the hackers might come from overseas trade protectionist groups or Alibaba's rivals.
Wu said Aliexpress, which had been in the test period since Aug. 6, 2009, would officially begin operations, although no timetable had been set.
A orator for the Municipal Public Safekeeping Bureau of Hangzhou, where Alibaba is based, said police would examine the incident.
Alibaba Group is an online business company, engaging in business-to-business global trade and retail sales. It was founded in 1999.
(Source: https://news.xinhuanet.com/english2010/sci/2010-04/19/c_13258636.htm)
a) From the above it is understandable to say that web applications do suffer loads of attacks. This can lead the association to suffer loss and more importantly clients can sue the company if their personal has been hacked.
The OWASP (Open Web Application Safekeeping Project) has published 10 risks that web applications are experiencing.
i. You are needed to name the top 10 risk to avoid hacking of your web application
ii. Elucidate in detail all the steps listed in OWASP as to how to avoid the first three attacks to happen.
b) Defense-in-depth is a dramatic departure from the transparent data corridor of the LAN. By pushing safekeeping into the network itself, the LAN changes from a public-access highway to a high safekeeping network of roads, serving gated communities.
Give the key attributes of secure networking when considering and implementing safekeeping into the LAN.
c) Defence-in-depth is not a product, like a outer limits of a firewall. In its place, it is a safekeeping architecture that calls for the network to be aware and self-protective. In studying the problem of adding defence-in-depth, there are keys strategies that safekeeping architects can use to change significantly the safekeeping posture of enterprise (venture) wired and wireless LANs (WLANs).
Name them in their particular order.