Reference no: EM131152086
Learning Outcomes
As per the Unit Guide, the following Unit Learning Outcomes are relevant to this project:
1. Demonstrate knowledge of concepts and roles of computer architecture and the influence of different layers of communication protocols.
You will be required to demonstrate knowledge of concepts and the architecture of computer networks including protocol layering, and services provided by layers.
2. Differentiate the types of networks, communication and user oriented protocols, and their influence on transmission speed, reliable delivery and security.
You will be required to demonstrate knowledge of the different types of networks and protocols and how they influence the various characteristics of networks for the transmission of data between devices on a computer network.
Question 1
Given the following network/s:
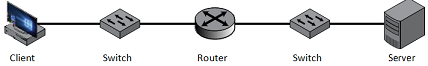
Consider the problem of transferring a large file via the web:
a) Identify how many networks are illustrated and what topologies is/are used in each network identified. Explain how you identified the networks and topologies in your answer.
b) For each of the five devices illustrated, indicate which layers of the TCP/IP protocol suite are certain to be found on that device and briefly explain why.
c) In the Week 1 slides / prescribed reading, it is mentioned that addressing is required at all layers except the physical layer. If this is true, explain how the physical layer will be able to deliver/direct the data to its intended destination. Refer to the above scenario/network when explaining your answer.
Question 2
a) Given that electromagnetic waves can travel at the speed of light, briefly explain how different signals can arrive at different times when transmitted at the same time. Consider both wired and wireless media in your answer.
b) Consider a digital signalling approach that uses only two voltage levels to represent binary data and achieves a data rate of 1Mbps. Explain how increasing the number of voltage levels could potentially increase the data rate and briefly discuss the potential problems that may be encountered.
c) A network administrator has identified that several paths throughout the organisation's network are experiencing significant latency. Given that latency consists of propagation time, transmission time, queuing time, and processing delay, discuss how each of these could potentially be reduced, addressing the identified problem.
d) Consider the Manchester and Differential Manchester encoding schemes.
i. Using the same input of 8 bits, draw an illustration of both schemes. For the input sequence, you may choose any 8 bits however must include both 1 and 0 bits.
ii. Explain how these schemes achieve self-synchronization.
iii. Explain the relationship between DC components and baseline wandering and how these schemes resolve this problem.
e) Consider the frequency-division multiplexing and time-division multiplexing techniques. Give an example where these two techniques could be used at the same time and explain how they are used.
Question 3
a) A colleague is developing a new protocol that will be implemented at the network layer. A key requirement of this new protocol is that data must be delivered in order. There are two data-link technologies to choose from, one is a datagram network and the other is a virtual-circuit network. Identify and discuss two advantages and two disadvantages of each technology.
b) Consider a scenario where a computer is attempting to send data to a device on the same network however the destination is not responding to ARP requests. Identify and briefly explain three reasons why this may occur. Note that the possibilities of the devices being turned off and/or not connected to the network have already been eliminated.
c) Refer to the figure shown on Week 3 Slide 49 for the calculation of CRC codes. Demonstrate the generation of the CRC code using the same approach (same divisor and number of redundant bits) using the 8-bit number 11001101 as input.
d) Consider the following three 16 bit data elements:
1100 1100 1100 1100
0101 1100 0101 1100
0001 0001 0001 0001
Demonstrate the calculation of the 16-bit Internet checksum for this input data.
|
Design is relational data model for library
: This design is a relational data model for a library in a small town. The library contains books, videos, newspapers, and magazines that can be checked out. It also contains reference books, videos, magazines, and newspapers that cannot be checked ou..
|
|
What credit damage was corrected
: Have you, a family member, or a friend been a victim of identity theft? How did it happen? Describe the resolution process- ex. how much time did it take, what credit damage was corrected?
|
|
Create the positioning and branding portion
: Create the Positioning and Branding portion of the Marketing Communications Plan using the business and information presented in the case study
|
|
Beneficial to the human spirit
: Janine is a herbalist, preparing certain natural tonics she believes to be "beneficial to the human spirit." Her activities are located in a province which does not regulate such matters.
|
|
Demonstrate the calculation of the 16-bit internet checksum
: Demonstrate knowledge of concepts and roles of computer architecture and the influence of different layers of communication protocols.
|
|
Is gay marriage morally permissible or is it wrong
: Assuming that lawmakers could all come to an agreement on how to legally regulate the practice of prostitution (for adult male and female prostitutes), would it be morally wrong to do so or is it morally permissible?
|
|
Regional economic integration in africa
: Regional Economic Integration in Africa. Who comprises the group? Do sub-groups exist? If so, who are they? What was the origin?
|
|
Identify a particular area of the wto
: Identify a particular area of the WTO Provide an overview of the topic. Explain in detail the agreement, and
|
|
What are the total return and the current yield
: What are the total return, the current yield, and the capital gains yield for the discount bond in Question #3 at $887.00? At $1,134.20? (Assume the bond is held to maturity and the company does not default on the bond.)
|