Reference no: EM131938408
Assignment: Network Routing and Switching
PART A
Question 1
What is the maximum size of an IPv4 header?
Question 2
What is the bit size of the port address in a UDP header?
Question 3
What is the default mask for a class A address in CIDR notation?
Question 4
A host needs to send a message to a local node. The host has the IP address of this local node but not the MAC address. What protocol should it use to obtain this MAC address?
Question 5
The following is an abbreviated IPv6 address:
FD80:3:A7A::20:0:3E
Write the full (expanded) address of this abbreviate IPv6 address.
Question 6
In a TCP connection, the value of cwnd is 6000 and the value of rwnd is 7000. The host has sent 4,000 bytes, which have not been acknowledged. How many more bytes can be sent?
Question 7
What is encapsulation in network protocols?
Question 8
Layer 1 and layer 2 of the OSI model are sufficient to support the operation of a network in the delivery of data. Why then was layer 3 introduced? Briefly explain.
Question 9
What is a Partially Qualified Domain Name (PQDN)? Explain.
Question 10
What is this IPv6 address also known as: ::1/128 ?
Question 11
What is an Autonomous System in networking context?
Question 12
Give two pieces of information that a DHCP server provides to a client.
Question 13
If a router using RIP has five expiration timers running, what is the maximum possible number of periodic timers that the router can have?
Question 14
What is a DNS resolver? Explain.
PART B
Question 1
An organisation has been allocated a block of classless addresses by the ISP:
142.39.51.16/30
List all the addresses in this range. Then identify those from your list: the network address, the addresses that can be used by hosts, and the direct broadcast address.
Question 2
An organisation has been granted a block of addresses which starts at 32.175.40.0/22. Create the following 8 subnets for this organisation:
(a) 1 subnet with 512 addresses.
(b) 3 subnets with 128 addresses.
(c) 4 subnets with 32 addresses.
Give your answer by copying and completing the following table in the examination Answer Booklet.
|
Number of addresses
|
Subnet address (including mask)
|
|
512
|
|
|
128
|
|
|
128
|
|
|
128
|
|
|
32
|
|
|
32
|
|
|
32
|
|
|
32
|
|
Question 3
The following is an ICMPv6 message fragment with its header (in hexadecimal): 01 04 B1 B5 00 00 00 00 00 00 00 00 00 .. ..
Identify the information that is carried in the header, and state their values. What type of ICMPv6 message is this? What is the message?
Question 4
The figure below shows the configuration of a hypothetical section of the Internet.
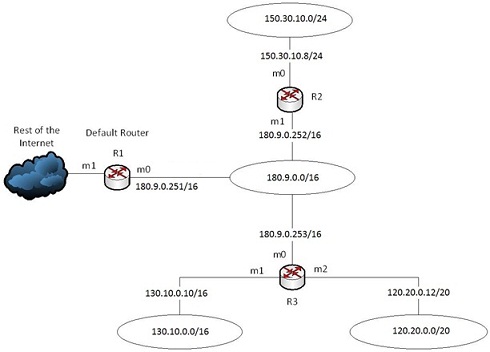
Construct the routing table of Router R3 for this configuration by copying and completing the following table in the examination Answer Booklet. Add or remove rows from the table as necessary.
|
Mask
|
Network address
|
Next-hop address
|
Interface
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
PART C
Question 1
In a communication between a client and a server, TCP is used to establish a network connection. This connection is established before any data is exchanged between the client and the server.
Describe the 3-way handshake that establishes this connection. Use suitable diagrams to support your description. Your diagram(s) and explanation must be clear. Use your own words to describe, and do not copy directly from any source including the textbook.
Question 2
IPv6 was proposed to address various limitations and weaknesses in IPv4. Identify six key changes that were introduced in IPv6, and briefly explain them. Use your own words to describe, and do not copy directly from any source including the textbook.
Question 3
Intradomain routers use the Distance Vector routing protocol and the Link State routing protocol. Compare and contrast the features of the Distance Vector routing protocol and the Link State routing protocol.
Do not simply describe the mechanism of a specific protocol. Use your own words to explain, and do not copy directly from any source including the textbook.
Question 4
In the area of wireless communications, LTE technology is used in mobile and data networking. Identify six key features of LTE technology, and briefly describe how these features provide benefits to mobile data communications.
Be clear and specific in your answer. Use your own words to explain, and do not copy directly from any source including the textbook.