Reference no: EM132371906
Assessment item : Theory and Simulation Exercises
Task
Using Packet tracer implement the following tasks based on the network topology of a small business given below. Smart Univ Ltd has three branches: Albury, Bathurst and Wagga site. Each site has Admin Office to manage the local business. Wagga site has three buildings where has two major departments: Student group and Staff . Its Wagga office controls the connection between the Internet server and Internet Service Provider (ISP). Examine the network requirements and complete the following questions to make the company network service running.
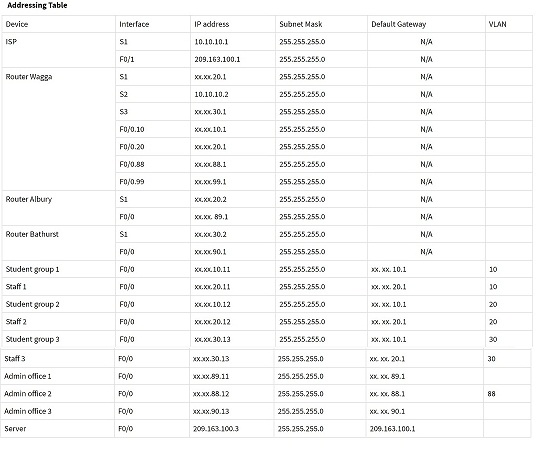
Please use your last 4 digits of your student ID as the first two octets of your network address. Keep other bits same as what are shown in the addressing table and the figure below. For example, if your student ID is 11567890, using the last 4 digits (7890). your main network address will be 78.90.0.0.
Consider the following Topology in the figure below:
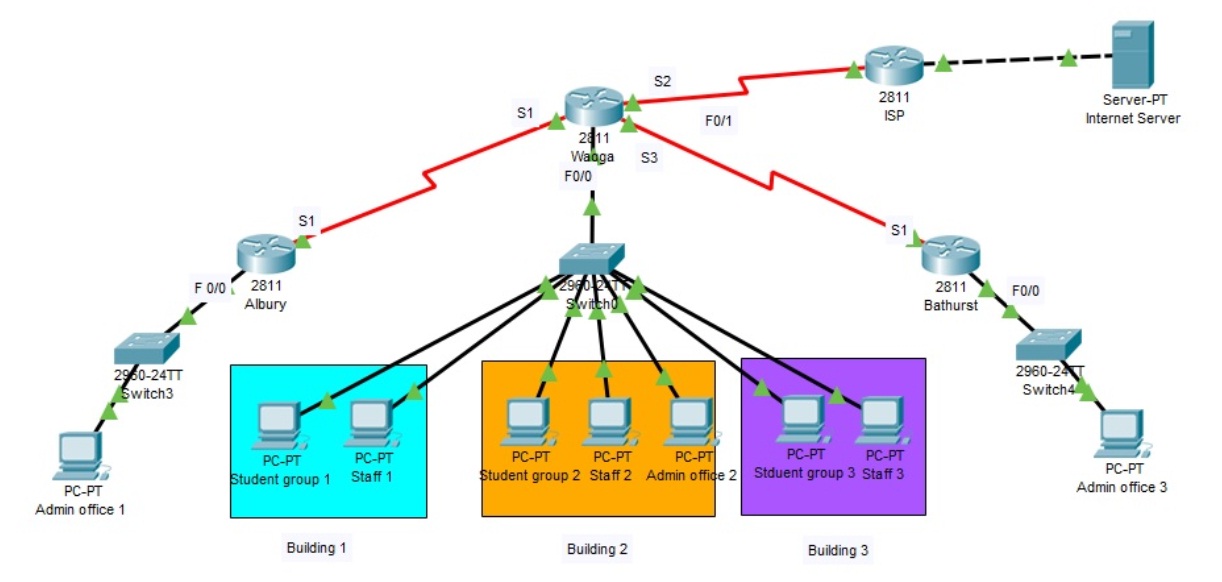
VLAN Table
|
VLAN
|
Name
|
|
10
|
Student group
|
|
20
|
Staff
|
|
88
|
Admin office 2
|
|
99
|
Native
|
You need to use Packet Tracer to implement the given topology and to complete the following tasks: Part A: Switching and VLANs
1. It is quite important to lock down access and install strong security features on PCs and servers. It is important that your network infrastructure devices, such as switches and routers, are also configured with security features. What will be the best practice to secure your switch?
2. Configure four VLANs as required on the switch and enable Trunking on switch.
3. Configure inter-VLAN routing on Router wagga based on the Addressing Table.
4. Configure static routes on routers to build up full connectivity between each site to ISP and Internet server.
5. Verify connectivity by making sure all the PCs can ping the Internet server and ISP.
6. Explain and analyse the routing process of routers in the case of ping from Student group 1 to the Internet server.
Please save your configured packet tracer file with the name of "PT_your studentlD_partA"
Part B Network Security
7. In order to improve the network performance and security, ACLs is recommended. Please explain what is the ACL ?
8. How can ACLs help with the required tasks?
9. What are the principles of applying ACLs?
10. How to block VLAN 10 to visit ISP? Please write down the ACL statement(s) accordingly
Please save your configured packet tracer file with the name of "PT_your studentlD_partB"
Rationale
This assessment task will assess the following learning outcome/s:
• be able to configure and troubleshoot networks to improve efficiency and security.
• be able to configure, verify and solve a variety of problems involving Virtual Local Area Networks.
In this assessment item, tasks are designed to reinforce the application of configuring routers for inter-VLAN communication and configure static routes to reach destinations outside of your network. Your ability demonstrate your skills at configuring inter-VLAN routing, static and default routes are also included.