Reference no: EM131016431
Task
This assessment item is to produce a short report by investigating and addressing some key topics for this subject. Note answering these questions will help you build some understanding for the next assessment item as well as for the entire subject material. It is expected that answers to the assignment questions be succinct (i.e. precise and concise) with all sources of information fully referenced as per APA referencing style. You have to reference the text book and any additional material you have used in your answers.
Note that the guide for APA referencing is provided in the Resource section of Interact site.
Answers MUST be written in your own words. If an answer contains more than 20% direct quote (referenced or unreferenced) 0 marks will be awarded for this question.
One or two sentence answers will be too short and only receive low marks. Answers longer than 1.5 pages (12 point font, single line spacing) may incur a penalty if too much non-relevant information is stated.
For mathematical and subnetting questions it is expected that you show intermediate steps of your working. Just stating the correct solution will result in low marks, on the other hand if the working is correct and you only made minor mistakes, you will still be awarded marks, even though the final answer is wrong.
Question 1
Describe the differences between a repeater, a switch and a router. Why is a router generally more expensive and complex than a switch, and why is a switch generally more complex and expensive than a repeater?
Question 2
(Show your working and give a short explanation for each answer.)
Designing IP Addressing schemes and configuring IP Addressing is a common activity undertaken by network engineers. Consider an ISP is granted a block of addresses starting with 150.80.0.0/16. The ISP needs to distribute these blocks to 2600 customers as follows:
a. The first group has 200 medium-size businesses; each needs approximately 128 addresses.
b. The second group has 400 small-size businesses; each needs approximately 16 addresses.
c. The third group has 2000 households; each needs 4 addresses.
Design the sub blocks and give the slash notation for each sub block. Find out how many addresses are still available after these allocations.
Question 3
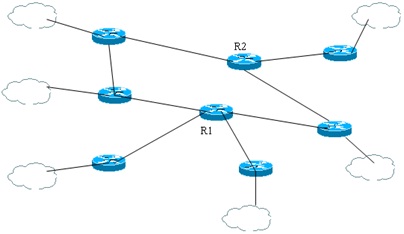
Consider the diagram below. Which of the two central routers (R1 and R2) is more critical for network operations and why?
Question 4
Contrast and compare distance vector routing with link state routing.
Question 5
Discuss the role ICMP plays in extending the IP protocol architecture? Looking into the structure of the error reporting ICMP messages, what is the purpose of including the IP header and first 8 bytes of datagram data?
I need top quality with 100% origniality and with no plagarism