Reference no: EM131183147
THE SCENARIO
The Advanced Digital Computer Company is a new company with its Head Quarters building in the city, and with branches in Parramatta, Hornsby and Sutherland. In addition, there are two small home offices in Bankstown and Epping. There are WAN connections between each site and Head Office, with all Internet access through the Head Office site.
The Advanced Digital Computer Company is a retail company for all types of computing devices. The company is planning a restructuring of its network to allow for an expected 100% expansion over the next 5 years. Whilst the numbers of sites are expected to remain the same, the number of employees, and so end computing devices, is expected to double. However, the server farm, currently 4 servers, is expected to be adequate for the foreseeable future.
The Advanced Digital Computer Company has consulted your group to provide a detailed Networking Plan. To assist you the below diagram is supplied.
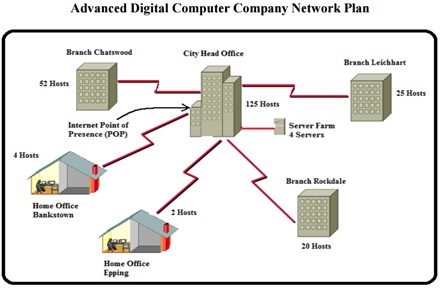
REQUIREMENTS
You must design the network requirements for the Advanced Digital Computer Company. As the network consultant you will be required to develop a plan for the Company network, including all costs, for all of the following:
1. The type of media you propose to use. This must be adequate to allow for a 100% expansion of the Company network within 5 years, and must be sufficient for all bandwidth requirements for each Company site. It should also be sufficient for increased bandwidth needs in the future. Whilst the actual lengths of media chosen are not required, the cost of media chosen should be included as a cost per metre price. You must justify your choice of media. Remember this might include copper, fibre and wireless options. The serial links between each site will be supplied by the company's ISP and are therefore not to be included in the above media requirements.
2. You are required to subnet the Company's network IPv4 Address using VLSM as appropriate. You will be required to provide summary tables with IP Address ranges for all hosts in your network. When allocating addresses you must allow enough addresses for the 100% expected future expansion of hosts for the Advanced Digital Computer Company. As well, you need to allocate one (1) printer for each 50 computers (or part thereof) on each subnet. If there are, for example, 70 computers required on a subnet, then two printers are required for that subnet. Printers will have the last usable address/es for the subnet to which they belong. The servers will be located in a separate subnet, and must be allocated static IPv4 Addresses within that network. The number of servers is not expected to grow.
3. The ADC Company is anticipating a move to IPv6 in the future, and so needs to use a Dual Stack environment for IPv4 and IPv6 addresses. You are required to address the network for IPv6.
4. You must detail the hardware (ONLY switches, routers) that the ADC Company will require. This must include full reasons for selecting particular hardware, which must be adequate for the ADC Company's requirements. Again, consideration must be made with regard to future expansion and bandwidth requirements. The details about computers, servers and printers are not required.
5. You must justify the type of network topology you propose to use at each ADC Company location. A topology diagram for each location should be included in your report.
6. Communication on the Internet is essential. Select and fully justify the type of Internet access you propose to have for this Company. This must be scalable to allow for future growth and needs. The Point of Presence (POP) is located at Head Office.
Additional Information
1. Apart from the IP Addresses, you are not required to supply any WAN link information. This included serial cables, VPN connections, or any security issues relating to those links.
2. Head Office employees are in three separate networks as follows:
a. Sales 60 Hosts
b. Marketing 35 hosts
c. Accounts 30 Hosts
3. There will be a Server Network, with 4 Servers, for the entire Company. This will be situated in a separate LAN in the Head Office building. It is expected that the 4 servers will be sufficient for the next 5 years, and so will not be subject to the 100% growth requirement.
4. All branch offices and Home Offices can be considered an extension of the Head Office network, and so the IP Addresses allocated must be reflected in the overall addressing scheme for the company. The only media requirements required are those internal for each site.
5. Hardware (such as routers and switches) should reflect expected usage. Therefore, low usage environments such as those for the Home Offices, would require different hardware than high usage areas, such as those of the Head Office.
6. Internet Access for the entire company, the Point of Presence (POP), is through the Head Office. This connection should be sufficient for all current users, and scalable to allow for the expected increase over the next 5 years.
Packet Tracer
Model You are required to make a Packet Tracer Model of this network. This model should include the following:
1. All routers and switches you propose for the network.
2. All routers and switches need to be named on the topology diagram.
3. All interconnections between these routers and switches.
4. Addresses, both IPv4 and IPV6 (where appropriate) configured on all devices, and placed on the working model topology.
5. All subnets must be placed on the model.
6. A single host PC is required for each subnet. This PC should have an appropriate IPv4 address configured on it. IPv6 Addresses for PCs is not required. Do not include any printers in this model.
7. Routing, as shown below in the documentation, needs to be included.
8. The connection for the Internet, at the point of presence, should be shown by a connection on the router in the Main Distribution Room.
9. The link to the Internet does not require an IPv4 or IPv6 address. It is assumed that this link will be managed by the ISP.