Reference no: EM132219617
Assignment - Propose/design a VPN for the scenario given below including LAN and WAN settings.
Purpose of the Assessment
The purpose of this assignment is to implement a VPN network for an SME (small and medium sized enterprise), details are given below.
A thorough verification and evaluation analysis should be presented to meet he ULO mapping in the Unit Description.
In preparing the assignment, students should acquire not only the knowledge of current technical aspects of IP networks but also research, data collection, analysis and writing skills.
Assignment Description
There are two parts to this assignment, part A and part B.
A. Design and model Implement (in Netsim) of VPN for Sigma Inc. by addressing the following criteria. See detailed instructions in the next section.
B. Presentation
Part A: Design and Report
Two broad areas to be considered for VPN network design in this assignment are as under;
1. Propose/design a VPN for the scenario given below including LAN and WAN settings.
2. Configure and implement the network at low-level design, this part should be done using BOSON NETSIM Simulator.
Contents must include:
High-level network design summary Solution Design
i. Network Topologies
ii. IP addressing
iii. Configuration details and screenshots to present low-level design
iv. Verification methodologies and evaluation analysis
Scenario
In this scenario, Sigma, Inc. wants to establish a VPN between the subnets of its Human Resources and Finance departments through a system models which does not have any firewall deployed at either end. Both systems will act as VPN gateways. In terms of VPN configurations, a gateway performs key management and applies IPSec to the data that flows through the tunnel. The gateways are not the data endpoints of the connection.
The objectives of this scenario are as follows:
- The VPN must protect all data traffic between the Human Resources department's subnet and the Finance department's subnet.
- Data traffic does not require VPN protection once it reaches either of the department's subnets.
- All clients and hosts on each network have full access to the other's network, including all applications.
- The gateway systems can communicate with each other and access each other's applications.
Details
The following figure illustrates the network characteristics of Sigma Inc.
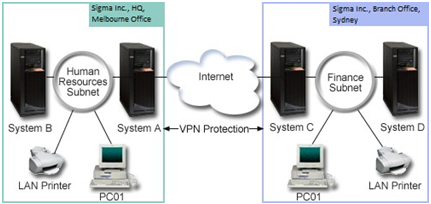
Figure-1: Sigma Inc. Office configuration
Human Resources Department
• System A acts as the Human Resources Department's VPN gateway.
• Subnet is 10.6.0.0 with mask 255.255.0.0. This subnet represents the data endpoint of the VPN tunnel at the Sigma Inc., Melbourne site.
• System A connects to the Internet with IP address 204.146.18.227. This is the connection endpoint. That is, System A performs key management and applies IPSec to incoming and outgoing IP datagrams.
• System A connects to its subnet with IP address 10.6.11.1.
• System B is a production system in the Human Resources subnet that runs standard TCP/IP applications.
Finance Department
• System C acts as the Finance Department's VPN gateway.
• Subnet is 10.196.8.0 with mask 255.255.255.0. This subnet represents the data endpoint of the VPN tunnel at the Sigma Inc., Sydney site.
• System C connects to the Internet with IP address 208.222.150.250. This is the connection endpoint. That is, System C performs key management and applies IPSec to incoming and outgoing IP datagrams.
• System C connects to its subnet with IP address 10.196.8.5.
Configuration tasks
You must complete each of these tasks to configure the branch office connection described in this scenario:
Completing the planning: The planning checklists illustrate the type of information you need before you begin configuring the VPN. All answers on the prerequisite checklist must be YES before you proceed with VPN setup.
Configuring VPN on System A: Complete these task to configure System A
Configuring VPN on System C: Follow the same steps you used to configure VPN on System A, changing IP addresses as necessary. Use your planning worksheets for guidance.
Starting VPN: After you have configured your VPN connection on System A and C you need to start your VPN connection.
Testing a connection: After you finish configuring both systems and you have successfully started the VPN servers, test the connectivity to ensure that the remote subnets can communicate with each other.
Part B: Presentation
Task B
The proposed network design will be presented in a 5-minute presentation during the week 12 Lab class. Presentation slides should be submitted in Moodle prior to the presentation for marking.