Reference no: EM13372966
Identifying Potential Malicious Attacks, Threats and Vulnerabilities
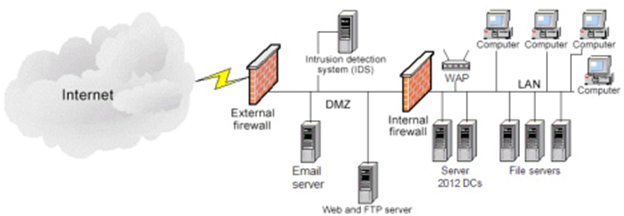
You have just been hired as an Information Security Engineer for a videogame development company. The organization network structure is identified in the below network diagram and specifically contains:
1) 2 - Firewalls
2) 1 - Web / FTP server
3) 1 - Microsoft Exchange Email server
4) 1 - Network Intrusion Detection System (NIDS)
5) 2 - Windows Server 2012 Active Directory Domain Controllers (DC)
6) 3 - File servers
7) 1 - Wireless access point (WAP)
8) 100 - Desktop / Laptop computers
9) VoIP telephone system
The CIO has seen reports of malicious activity being on the rise and has become extremely concerned with the protection of the intellectual property and highly sensitive data maintained by your organization. As one of your first tasks with the organization, the CIO requested you identify and draft a report identifying potential malicious attacks, threats, and vulnerabilities specific to your organization. Further, the CIO would like you to briefly explain each item and the potential impact it could have on the organization.
Write a four to five (4-5) page paper in which you:
1. Analyze three (3) specific potential malicious attacks and / or threats that could be carried out against the network and organization.
2. Explain in detail the potential impact of the three (3) selected malicious attacks.
3. Propose the security controls that you would consider implementing in order to protect against the selected potential malicious attacks.
4. Analyze three (3) potential concerns for data loss and data theft that may exist in the documented network.
5. Explicate the potential impact of the three (3) selected concerns for data loss and data theft.
6. Propose the security controls that you would consider implementing in order to protect against the selected concerns for data loss and data theft.