Reference no: EM131172998
Search:
1. Suppose you are given a set P of integers and another integer x. We wish to use a Θ(n2) algorithm to decide whether there are 3 integers in P and the sum of these three integers equals to x. Show your algorithm and indicate why its complexity is Θ(n2). (You can use pseudo code or by illustration only)
Recurrence:
2. Using a recursion tree, show the process how to solve the following recurrence in terms of the big O representation. Use the substitution method to verify your result.
T(n) = 4T(n/4)+cn
Sorting:
3. Can RADIX SORT shown in our textbook work correctly if we use QUICKSORT instead of COUNTING SORT to sort each individual digit? Justify your answer.
Data structures:
4. If we perform an inorder traversal on a Min Heap will we get the values in sorted order? Why or why not? Use a simple example to justify your answer.
Greedy algorithms and dynamic programming:
5. You have n programs p1, ..., pn with size m1, ..., mnMB (mega bytes). You have a disk that can store up to W MB. W is less than the total size of the programs. You are asked to use a dynamic programming solution to store the programs onto the disk so as to maximize the disk space utilization. In other words, you want to find a subset of programs such that its total size is maximized but has to be less than C.
6. Define U[i, w] as the maximum disk utilization of a disk with capacity w MB and programs p1,...,pi to be selected for storing it on the disk. Write a recurrence for U[i, w] and identify the boundary condition.
7. Consider the problem of making change for n cents using the fewest number of coins. Assume that each coin's value is an integer.
8. Describe a greedy algorithm to make change consisting of quarters (25 cents each), dimes (10 cents each), nickels (5 cents each), and pennies (1 cent each). Prove that your algorithm yields an optimal solution.
9. Give a set of coin value combination (the value of coins may not be limited to quarter, dime, nickel, or penny) for which the greedy algorithm does not yield an optimal solution. Your set should include a penny value so that there is a solution for every possible value of n. Use an example to justify your answer.
Tree and graph:
10. Given the following weighted undirected graph, show the order the edges would be added for building a spanning tree using Kruskal's and Prim's algorithm. Take the following figure as an example, order edges added using two algorithms. In addition, how many edges will be picked up to build the tree? Why? Show your process.
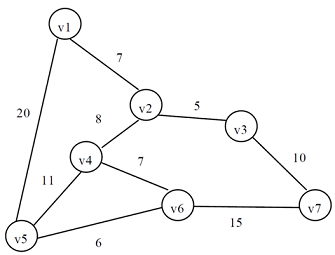
11. For each of the following, either draw a graph satisfying the given criteria or explain why it cannot be done. Your graphs should be simple, i.e. not having any multiple edges (more than one edge between the same pair of vertices) or self-loops (edges with both ends at the same vertex).
a. A graph with 3 connected components, 11 vertices, and 8 edges.
b. A graph with 3 connected components, 10 vertices, and 30 edges.
c. A graph with 3 connected components and 10 vertices. 9 vertices have degree 3 and 1 vertex has degree 4.
d. A graph with 6 vertices, of which 4 have degree 3, 1 has degree of 4 and 1 has degree 5.
|
Discuss at least two different types of operating systems
: Write an essay using Microsoft Word identifying and discussing at least two different types of operating systems. Include the advantages, disadvantages, and security concerns of each type of operating system.
|
|
Similarities between decision process and what managers do
: How do you think managers typically choose between several options?- What are the similarities between your decision process and what you think managers do?
|
|
Key components of supply chain management
: Determine the key components of supply chain management for the company you have selected. Determine three (3) major issues that could affect the structuring, sourcing, purchasing, and the supply chain of your organization. Provide a solution to e..
|
|
Calculate the resulting forces on this pair of doors
: The lock is 8 m wide. Calculate the resulting forces on this pair of doors, and draw a free-body diagram of this pair of doors showing the opposing pressure distributions
|
|
How many edges will be picked up to build the tree
: Given the following weighted undirected graph, show the order the edges would be added for building a spanning tree using Kruskal's and Prim's algorithm. Take the following figure as an example, order edges added using two algorithms. In addition,..
|
|
Examine the safety of your own personal food production
: Examine the safety of your own personal food production practices at home or at work. Point out key changes you should consider in order to improve your own food safety and / or changes that your employer should consider in order to improve food s..
|
|
Do you agree with given statement or not
: "An individual decision maker should process all relevant information and select the economically rational alternative."- Do you agree? Why or why not?
|
|
Explain the existing security situation in the organization
: Explain the design approach and rationale. Prove that the design meets the data rate requirements. Analyze the existing security situation in the organization. Identify the predominant electronic and physical threats to communications networks.
|
|
Part of a new project that the firm is planning
: The following activities are part of a new project that the firm is planning. If the project is planned using the critical path method, how would the network look? What is the critical path? Also, estimate the completion time for this project.
|