Reference no: EM131724115
Assignment: Introduction to Computer Networks
1. MAC Address, ARP, Switching and IP Forwarding (25 points. Approx. 30 minutes)
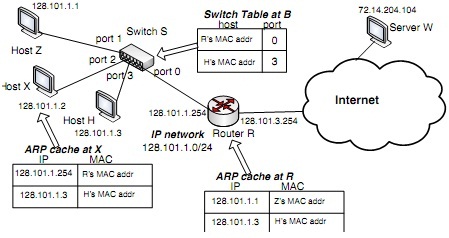
Figure 1: Switched network
Consider the following switched network (Figure 1), where we have one Ethernet switch S, connecting three hosts, host Z on port 1, host X on port 2 and host H on port 3, as well as an IP router R (default router for the hosts) on port 0. These hosts lie on an IP network with the network prefix 128.101.1.0/24. The IP address for the interface of router R that is connected to switch S is 128.101.1.254. The IP addresses for hosts Z, X and H are shown in the figure. Furthermore, the current switch (forwarding) table at switch S and the ARP caches at host X and router R are also shown in the figure.
(a) Suppose host X wants to send an IP datagram to host Z, and assume that host X knows the IP address of host Z (e.g., via DNS lookup).
Briefly explain how host X obtains the MAC address of host Z. Describe how switch S handles the ARP request and response messages, and builds its switch table.
Will router R also receive the ARP request? If your answer is affirma- tive, what action does router R take? What about the ARP response message from host Z?
After host X learns the MAC address of host Z. Briefly describe how the IP datagram is delivered from host X to host Z, paying particular attention to the actions taken by switch S, and router R if any.
(b) Suppose host X sends an IP datagram to host H instead of host Z. Repeat the above questions.
(c) Suppose now that host X wants to send an IP datagram to a remote server W outside the network. The IP address of server W is 72.14.204.104. Answer the following questions.
Since server W's MAC address is not currently in its ARP cache, will host X issue an ARP request for server W? Briefly explain your answer.
How does X know that it should forward the IP datagram to router R so that it can be delivered (via the Internet) to server W?
Briefly describe how the IP datagram is delivered from host X to router R, paying in particular attention to the actions taken by switch S and router
R. Moreover, please explicitly describe the source and destination IP and MAC addresses contained in the IP datagram and the encapsulating Ethernet frame.
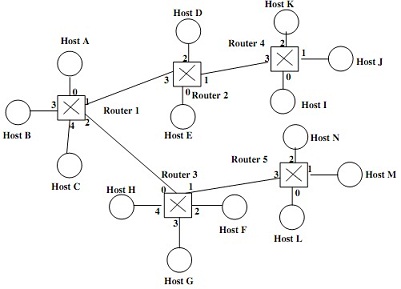
2: Figure for Question 6b.
2. Virtual Circuits
a. What is the key difference between virtual circuit and circuit switching? (one or two sentences should suffice!)
b. Consider the network shown in Figure 2, where the numbers beside the links connecting hosts and routers represents the port numbers of the routers. Please write down the virtual circuit translation tables for all the routers after the following connections are established in the order given below. You can assume that the VCI assignment always picks the lowest unused VCI on an outgoing link.
(1) Host A connects to host K.
(2) Host B connects to host J.
(3) Host B connects to host D.
(4) Host D connects to host F.
(5) Host E connects to host L.
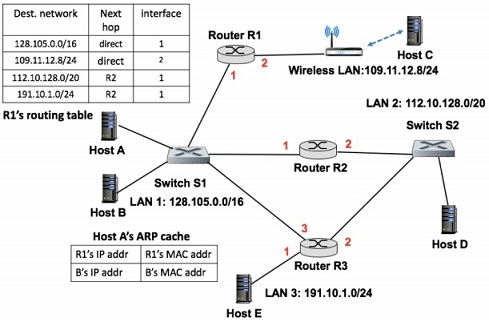
Figure 3: Figure for Bonus Question 6: IP Forwarding, Default Router and ICMP Re-Direct.
6. (Optional Bonus Question) IP Forwarding, Default Router and ICMP Redirect
Refer to Figure 3 and answer the following questions as concisely as you can. In answering these questions, you'll need to google and look up relevant information on ICMP Redirect, e.g., on wikipedia.
a. Consider the following scenario: host A wants to send an IP packet to host D, which is connected to LAN 2 (IP network prefix: 112.10.128.0/20). Since host D is not on the same IP network as host A. Hence host A will send it to its default gateway router R1. Describe the actions taken by router R1 (and subsequently at router R2) at both the network layer and data link layer for sending this IP packet to host D. You can assume that R1 has the MAC address of R2, and R2 has the MAC address of host D.
b. Continue the scenario in problem 8.a: suppose host A wants to send another IP packet to host D. Will host A still send it to router R1? Or will it send it to router R2? (Hint: if you did not mention ICMP Redirect message in your answer to problem 1.a, your answer is not complete].) Since host A does not have router R2's MAC address. Describe how host A obtains R2's MAC address using the ARP protocol.
c. Consider yet another scenario: suppose host A now wants to send an IP packet to host E, which is connected to LAN 3 (IP network prefix: 191.10.1.0/24). Host A will send it to its default gateway router R1, which will send it to router R2, based on its current routing table. Now let's assume that, based on the routing table at router R2 (not shown), it will send the packet to router R3 via its interface 1, namely, back to the same interface where it comes from. Will router R2 send an ICMP Redirect message to router R1, telling it to use R3 for destination network prefix 191.10.1.0/24? (Hint: ICMP messages are always sent to the source IP address of an IP packet.) More basically, can the network layer at router R2 tell whether router R1 or host A sends the packet to it? Briefly explain your answer.
d. Continue the scenario in problem 8.c: how will router R1 eventually knows that it can reach destination network prefix 191.10.1.0/24 directly via router R3 instead of router R2? Namely, changing the next hop from R2 to R3?
e. What might have happened that caused R1 to have a "non-optimal" route entry that has router R2 as the next-hop to the destination network prefix 191.10.1.0/24 instead of router R3 in the first place?