Reference no: EM13186477
Assignment on Mirror Mirror on the Ceiling: Flexible Wireless Links for the Data Center.
Please answer the following questions using the research paper:
1) Section 3.1:
If the distance between the sender and receiver is L and the ceiling height is hderive the expression of the propagation path length.
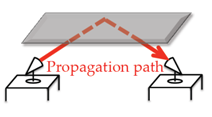
It is given as 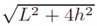 in the paper in section 3.1. Please show how this expression is achieved. You can draw a triangle to show your work.
in the paper in section 3.1. Please show how this expression is achieved. You can draw a triangle to show your work.
2) Section 4.2
Suppose the set of already scheduled links is {L1, L2, L3, L4, L5, L6} (same channel)
Using equation (3) how can we determine is link L7 can be added to the above set?
Show how the equation will be used step by step and explain each step verbally.
3) Section 4.2
Draw a simple graph to show conflict degree. Use channels as colors and show the algorithm step by step to color the graph. Explain what does thismean i.e. what have you constructed?
4) Give one idea how routing can be carried out in this research idea.
5) Give one idea how wired/wireless scheduling can be carried out in this research idea.
|
Compute the work done in joules
: Calculate the work done in Joules when one mole of an ideal gas, initially at P = 9 atm, T = 298 K is expanded isothermally to P = 1 atm if (a) the expansion proceeds against a onstant external pressure Pext = 1 atm; (b) the external pressure is r..
|
|
What is prisoner 1s dominant strategy
: Two suspects are arrested and charged with a crime. The police lack sufficient evidence to convict the suspects, unless at least one confesses. The police hold the suspects in separate cells and explain the consequences that will follow from the a..
|
|
State cyclohexanes substituted in the positions indicated
: For the cyclohexanes substituted in the positions indicated, identify the substituents as either axial or equatorial in chair conformers. For example, a 1,2-cis relationship means that one substituent must be axial and one equatorial.
|
|
Determine the duopoly firms constant marginal cost
: Suppose that in a duopoly firms have constant marginal cost MC = 10 per unit. Firm 1 faces demand function q1 = 100 - 2p1 + p2, while firm 2 faces demand function q2 = 100 - 2p2 + p1. What is the Nash equilibrium of this game. What is the Nash equ..
|
|
Draw a simple graph to show conflict degree
: Draw a simple graph to show conflict degree. Use channels as colors and show the algorithm step by step to color the graph. Explain what does thismean i.e. what have you constructed?
|
|
State what is the ph at half the euivalence point
: Acetic acid solution is titrated with NaOH solution. What is the pH at half the euivalence point?
|
|
What is the welfare effect of piracy
: A monopoly sells music CDs. It has a constant marginal and average total cost of $20. It faces two groups of potential customers: honest and dishonest people. The dishonest and honest consumers' demand functions are the same,Qh = Qd = 120 - P.
|
|
Derive the long-run total cost curve equation
: Assume that a monopoly's production function is Cobb-Douglas, Q = L^1/2 * K^1/2, where L is labor and K is capital. The demand function is P = 100 - Q. The wage rate, wL, is $1 per hour, and the rental rate of capital, wK, is $4 per hour. (a) Deri..
|
|
Implications or compatibility with the first welfare theorem
: "Since the indirect utility function, under standard assumptions, is quasi-convex in prices, randomization over equilibrium prices can be Pareto improving even if fundamentals are not stochastic." Assess this claim and its implications or compatibi..
|