Reference no: EM131183384
Question 1
(1a) The following are three terms used in data communication. For each term, (1) explain its meaning or functionality; (2) state the name of the OSI reference layer it belongs to; and (3) appraise the function of its OSI reference layer.
(i) Amplitude modulation
(ii) Subnet
(iii) Media access control
(1b) The following are three pairs of concepts used in data communication. For each pair of concepts, apply these concepts in real-time video streaming in Internet (such as Youtube) and appraise their differences.
(i) "Error concealment" and "Error resilient"
(ii) "Network delay" and "Network jitter"
(iii) "Shortest path routing" and "Flooding"
Question 2
(2a) Plan communication channel to transmit a Word document. This document has a size of 2,300,750 Bytes, and the signal level is considered as 2 since it needs binary representation to store the Word document information
(i) Consider a noiseless communication channel A with a bandwidth 384 KHz, appraise the data transmission rate that can be achieved in this communication channel A.
(ii) Consider a noisy communication channel B with a bandwidth 5 MHz and a signal-to-noise ratio 42 dB. Analyse how many minutes are needed to transmit 100 copies of this document.
(iii) Appraise how to apply the error detection code method to handle the noise during image transmission via the communication channel B.
(iv) Appraise how to apply the buffering method to reduce the jitter of the communication channel B.
(2b) A modem constellation pattern has five data points (denoted as (x,y)) at the following positions: (0, 2), (2, 2), (-1, -3), (1.5, -0.5), (0,
1). Answer the following three questions.
(i) Determine the data point that has the largest distance to the centre, and determine the data point that has the largest angle.
(ii) Name the modulation method(s) used in this constellation pattern. Justify your answer.
(iii) Implement the amplitude modulation technique only to modify this constellation pattern, without changing the number of data points.
That means there are five data points in your modified constellation pattern. Provide the coordinates of the data points in the modified constellation pattern.
Question 3
(3a) Consider a network topology illustrated in Figure Q3(a), where the numbers on the graph edges represent the transmission bandwidth (in terms of Mbps) of data transmission. For example, the transmission bandwidth from the node A to the node B is 2 Mbps.
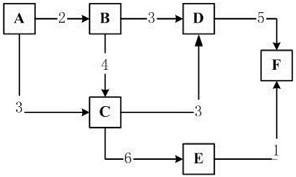
Figure Q3(a) A Network Topology.
(i) Apply the shortest path routing algorithm to diagram the best path from the source A to the destination F.
(ii) Describe the QoS factor "network delay", and appraise how to reduce network delay performance from the source A to the destination C.
(3b) Plan an IPv4 network for two banks A and B using consecutive IPv4 addresses. The bank B's IP addresses is larger than that of the bank A. These two banks A and B request 8192 and 2048 IP addresses, respectively. The ending IP address of the bank A is 218.66.31.255.
(i) Determine the IP address ranges of the bank A.
(ii) Determine the IP address ranges of the bank B.
(iii) Determine the subnet mask for bank A. Provide binary representation, decimal representation, and w.x.y.z/s notation.
(iv) Determine the subnet mask for bank B. Provide binary representation, decimal representation, and w.x.y.z/s notation.
|
Solid carbon--the c in the products side
: Suppose I give you a 250 g block of pure TNT and you detonate it. How much carbon residue (solid carbon--the C in the products side of the equation), in grams, would be produced?
|
|
Selling for according to the cost-of-carry model
: Suppose silver is currently selling at $4.23 per ounce in the spot market. Assume that the current risk-free rate (implied repo rate) is 3.75% and that silver contracts involve 5000 ounces each. Ignoring carrying costs and cash flows, what should the..
|
|
Small bottle of rubbing alcohol
: Let's make your next trip to the drugstore a little more interesting. Assume you are buying a small bottle of rubbing alcohol. How many molecules of isopropyl alcohol (C3H8O) are in a 50 mL bottle of isopropyl alcohol? The density of isopropyl alc..
|
|
Current dietary recommendation
: The current dietary recommendation is to consume less than 0.1 mol of sodium per day. This is about one teaspoon of table salt. It includes all salt and sodium consumed, including sodium used in cooking and at the table. The sodium content of a po..
|
|
Determine the data point that has the largest distance
: Determine the data point that has the largest distance to the centre, and determine the data point that has the largest angle. Name the modulation method(s) used in this constellation pattern.
|
|
Differantiate the types hypersensitivity reactions
: Differantiate the types hypersensitivity reactions that occur. Be sure to include examples
|
|
Possibility of gain or loss on operating exposure offset
: The possibility of a gain or loss on operating exposure offset by an opposite loss or gain on transaction exposure may appear contradictory. Explain why, when the currency in which a foreign subsidiary operates falls in value, the parent firm may exp..
|
|
What is the project''s payback period
: The director of capital budgeting for Big Sky Health Systems, Inc., has estimated the following cash flows in thousands of dollars for a proposed new service
|
|
Equity earnings may never result in actual receipt of cash
: Which of the following statements is true? Equity earnings may never result in the actual receipt of cash. Equity earnings are recorded when investment ownership is over 50%. Equity earnings are recorded when investment ownership is 100%. Equity earn..
|