Reference no: EM13810723
Assignment: Network Consultation for DesignIT
This assignment contains two (2) Sections: Network Consultation Proposal and Network Consultation Presentation. You must submit both sections as separate files in order to complete this assignment.
The owners of DesignIT, who recently purchased 56'x36' space for their expanding business, have asked you to place a bid on a consulting job. DesignIT is a graphic arts company that, up until now, had contracted work out to temporary design services. The new space will allow them to hire two (2) full time designers and a receptionist.
Description of space purchased:
- 4 Cubicles
- 1 Office
- 1 Server room
- 1 Reception desk
- 1 Conference room
Below is the design of the space purchased:
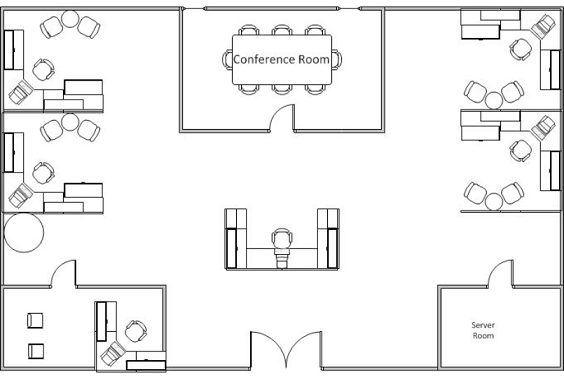
If the design doesn't show it should be in the attachments.
Using the building layout, your role is to provide DesignIT with a network design that interconnects the following considerations:
- DesignIT plans to relocate three (3) servers already configured as follows:
- 1 Web Server - Microsoft IIS Server
- 1 File Server - Microsoft Server 2008
- 1 Server - Server 2008 Small Business Server
- DesignIT has requested that the design include the following:
- High speed Internet access
- Firewall
- Antivirus / malware protection
- Six (6) computers
- Three (3) color laser printers
- Wireless access for portable devices
- DesignIT has requested the consideration of all interconnected devices and wiring, along with speeds, for best performance.
Section 1: Network Consultation Proposal
Create a cost analysis, and develop a proposal for the company.
- Write an five to seven (5-7) page proposal in which you:
- Recommend one (1) suitable network design.
- Suggest one (1) network architecture.
- Suggest LAN and Wireless LAN (WLAN) wiring considerations.
- Recommend hardware options and costs.
- Suggest security considerations for:
- Firewall
- Antivirus software
- Recommend software options and costs.
- Outline the labor costs, equipment costs, and service costs for your suggested design in table format.
- Identify the single point of failure, and recommend potential mitigation strategies.
- Use at least three (3) quality resources in this assignment. Note: Wikipedia and similar Websites do not qualify as quality resources.
Section 2: Network Consultation Presentation
Use Microsoft PowerPoint or an open source alternative to present your findings to the client.
- Create a five to ten (5-10) slide presentation in which you:
- Outline the recommendations from your written proposal in Section 1.
- Provide general speaking notes that you would use to highlight non-visual content.
|
What were some of basquiat''s inspirations
: 1) What were some of Basquiat's inspirations for his paintings? 2) How did Basquiat's paintings evolve during his short but prolific career? 3) What made Basquiat different from other artists of his generation? (Please cite evidence from the document..
|
|
The use of performance enhancing drugs
: An opposition research paper on the use of performance enhancing drugs in major league baseball. How come they use it, what factors benefit ticket sales, what do crowds want to see in a game. need 5 resources APA citation.
|
|
Rationale for identified target population
: Rationale for identified target population
|
|
Socially responsible investments in the northwest
: Heres a bit of background information we didnt cover in our phone conversation KMS Financial Services, Inc. has been in business since 1971 and is one of the largest Northwest based independent investment firms we offer one of the widest selections o..
|
|
Create a cost analysis and develop proposal for the company
: This assignment contains two (2) Sections: Network Consultation Proposal and Network Consultation Presentation. You must submit both sections as separate files in order to complete this assignment. Create a cost analysis, and develop a proposal for..
|
|
Provide a tentative outline of the paper
: Explain what the issue is with the topic and explain your stance on it, state the thesis statement ( a complete sentence ), provide a tentative outline of the paper, and an explanation of why the topic chosen.
|
|
Analyze marketing strategies in reaching markets
: Analyze marketing strategies in reaching markets with their products or services - Continue with a detailed description of marketing management strategies used in the implementation of the marketing plan.
|
|
Define project management
: Define project management and explain its importance to the business world. Explain project life-cycle management and the benefits of project management to an organization.
|
|
Determine strategies to resolve conflict within organization
: Determine strategies to resolve conflict within organizations
|