Reference no: EM13811160
Part I: written exercises:
1. Begin with the following binary search tree, draw the BST that results after the operation or sequence of operations is performed. (All questions are independent and each question starts from the BST as following)
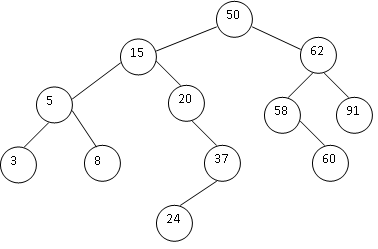
a. Insert 7
b. Insert 7, 1, 55, 29, and 19
c. Delete 8
d. Delete 8, 37, and 62
e. Insert 7, delete 8, insert 59, delete 60, insert 92, delete 50.
f. Display the output produced by an inorder traversal
g. Display the output produced by a preorder traversal
h. Display the output produced by a postorder traversal.
2. For the arithmetic expressions below, draw a binary tree that represents the expression, and then use tree traversals to find the equivalent prefix and postfix expressions.
a. (A-B)-C
b. A/ (B-(C-(D-(E-F))))
c. ((A*(B+C))/(D-(E+F)))*(G/(H/(I*J)))
3. Construct the Huffman code for the Java keyword and weights given in the following table.
|
Words
|
Weight
|
|
int
|
0.30
|
|
main
|
0.30
|
|
while
|
0.05
|
|
if
|
0.20
|
|
for
|
0.15
|
Part II: programming exercise
Start with the tree.java program (Listing 8.1) and modify it to create a binary tree from a string of letters (like A, B, and so on) entered by the user. Each letter will be displayed in its own node. Construct the tree so that all the nodes that contain letters are leaves. Parent nodes can contain some non-letter symbol like +. Make sure that every parent node has exactly two children.
Don't worry if the tree is unbalanced. Note that this will not be a search tree; there's no quick way to find a given node. You may end up with something like this:
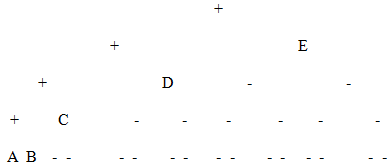
One way to begin is by making an array of trees. (A group of unconnected trees is called a forest.) Take each letter typed by the user and put it in a node. Take each of these nodes and put it in a tree, where it will be the root. Now put all these one-node trees in the array. Start by making a new tree with + at the root and two of the one-node trees as its children. Then keep adding one-node trees from the array to this larger tree. Don't worry if it's an unbalanced tree. You can actually store this intermediate tree in the array by writing over a cell whose contents have already been added to the tree.
The routines find(), insert(), and delete(), which apply only to search trees, can be deleted. Keep the displayTree() method and the traversals because they will work on any binary tree.