Reference no: EM132476916
Section A: MULTIPLE CHOICE
Directions: Choose the correct answer by highlighting it with green.
Question 1. You are the senior administrator for a bank. A user calls you on the telephone and says they were notified to contact you but couldn't find your information on the company website. Two days ago, an email told them there was something wrong with their account and they needed to click a link in the email to fix the problem. Hey clicked the link and filled in the information, but now their account is showing a large number of transactions that they did not authorize. They were likely the victims of what type of attack?
A. Spamming
B. Phishing
C. Pharming
D. Escalating
Question 2. Assume that you are working as information security analyst in HSBC bank. You are asked to choose the right risk management tool that uses an expert knowledge database to walk the user through a risk assessment. Which of the following tool shall you select?
A. COBRA
B. FRAP
C. Risk Watch
D. OCTAVE
Question 3. ISACA refers to testing for strong controls. What is the best description of a strong control?
A. Effective implementation of multiple controls targeting the same objective.
B. Preventative controls that stop the problem from ever occurring.
C. Using at least one control in each of the three categories of preventative, detective, corrective.
D. Implementing comprehensive pervasive controls inside of an ERP application.
Question 4. An IS auditor is performing a review of an application and finds something that might be illegal. The IS auditor should do which of the following?
A. Disregard or ignore the finding because this is beyond the scope of this revew.
B. Conduct a detailed investigation to aid the authorities in catching the culprit.
C. Immediately notify the audience of the finding.
D. Seek legal advice before finishing the audit.
Question 5. What is the principal issue surrounding the se of CAAT?
A. The capability of the software vendor.
B. Possible cost, complexity, and the security of output.
C. Inability of automated tools to consider the human characteristics of the environment.
D. Documentary evidence is more effective.
Question 6. Which of the following information security model is a set of concepts and techniques that is used for managing IT infrastructure development and operations?
A. COSO
B. COBIT
C. ISO
D. ITIL
Question 7. Identify the name of the risk that may occur if the router does not catch spoofed IP addresses during audit process.
A. Inherent Risk
B. Control Risk
C. Detection Risk
D. Business Risk
Question 8. A risk is a likelihood of a threat source taking advantage of a vulnerability to an information system. Risks left over implementing safeguards s know as:
A. Leftover Risks
B. Residual Risks
C. Remaining Risks
D. Exposures
Question 9. The members of the audit committee must NOT be?
A. Financially illiterate
B. Composed of business executives
C. Provide advice to the executive accounting officer
D. Promoting positive working relationship
Question 10. What is the purpose of the audit charter?
A. To engage external auditors
B. To grant responsibility, authority, and accountability
C. To authorize the creation of the audit committee
D. To provide detailed planning of the audit
Section 2: ESSAY
Directions: Answer the following items. Write your answer under each question.
Question 1. During risk management planning your team has identified three risks with probabilities of 10%, 50%, ad 35%. If the first two risks occur, they will cost you 5,000 USD and 8,000 USD; however, if the third risk occurs it will give you benefit of 10,000 USD. Determine the expected monetary value of these risk events.
Question 2. The accounting section of SPUP requires an application to process expense vouchers. Each voucher must be input by one of many accounting clerks, verified by the clerk's applicable supervisor, and then reconciled by an auditor before the final settlement check is produced. Which access control technique should be built into the application to best serve these requirements and describe this access control in brief?
Question 3. BDO plays a leading role in developing e-banking services and looking for high standard security. The bank operates through a network of 54 branches and offices throughout the country and offers a wide range of products and services. It needs to follow an information security standard which is beneficial for all its 54 branch managers, IT users, and auditors. Which is the best information security standard is suitable for this? Describe the structure of this standard.
Question 4. Computer-Assisted Audit Techniques (CAATs) are a growing field within the audit profession that an auditor (external or internal) uses as Section of their audit procedures. As an auditor identify and list any four illegal activities that are found by CAAT tools during auditing stage.
Question 5. During audit planning, several documents are produced in support of their project. Which one is used to identify the members of the audit team according to the person responsible for specific tasks in order to gain funding and ensure quality?
Question 6. Assume that you are working as an information security analyst. You are asked to create MC Cumber Cube to find a solution for below mentioned problems. Develop a security assurance model by using MC Cumber Cube framework or this scenario.
Domain Attack Vector Information State Countermeasure Security Goal
Question 7. You are asked to create evidence during our audit stage. Find out any two types of audit evidence ad provide the objective of the audit evidence with an appropriate example for each one.
Type of Audit Evidence Objective/Description
Section 3: ANALYTICAL QUESTIONS
Directions: Answer the following items. Write your answer under each item.
Question 1. A company is dedicated to offer a comprehensive range of security products and services which comply with the highest international industry standard requirements. It offers solutions in many security areas such as authentication, identity management, secure managed file transfer, data leakage prevention, network security, compliance certifications (ISO 27001), professional security services, information security training and digital forensics consulting.
This company is facing a number of information security threats. Using the following table, calculates SLE, ARO, and ALE for each threat category listed. [Just fill-in the blank cells].
|
Threat
|
Cost per Incident
|
Frequency of Occurrence
|
SLE
|
ARO
|
ALE
|
|
Programmers Mistake
|
$5000
|
1 per week
|
$5000
|
|
|
|
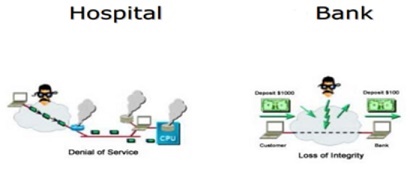
Denial of Service
|
$2500
|
1 per quarter
|
|
4
|
$10,000
|
Question 2. Assume that you are working as an auditor n BDO. As an auditor, give four (4) of your responsibilities while planning detailed audit objectives.
Question 3. Illustrate the overview of Audit Process Diagram.
Question 4. Read carefully the following Threat Rating Table which indicates the impact level of the risk in an organization.
|
Rating
|
High
(Impact Value is 3)
|
Medium
(Impact Value is 2)
|
Low
(Impact Value is 1)
|
|
Damage potential
|
The attacker can weaken the security system; get full trust authorization; run as administrator; upload content
|
Leaking sensitive information
|
Leaking nonsensitive information
|
|
Exploitability
|
A beginner programmer could make the attack in a short time.
|
A skilled programmer could make the attack.
|
The attack requires an extremely skilled person and in-depth knowledge every time to exploit.
|
|
Affected users
|
All uses, key customers
|
Some users
|
Very small percentage of users, affects unknown users
|
Based on the table above, fill-in the table below by specifying the impact level (High/Medium/Low) of the threat rating.
|
Threat Scenario
|
Damage Potential Rating
|
Exploitability Rating
|
Affected Users Rating
|
|
Attacker obtains authentication credentials by monitoring the network
|
High
|
|
|
|
SQL Injection Attacks
|
|
Low
|
|