Reference no: EM13864312
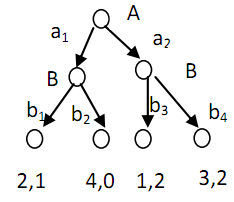
1. In the game below, find all subgame-perfect Nash equilibria (there are two). Identify the path through the tree that each one represents, and the utilities of each player. Does the game have any Nash equilibria that are not subgame perfect?
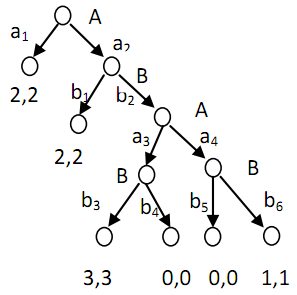
2. Compute the subgame perfect Nash equilibriua in the game below.
3. Alice and Bob own a dollar, which they need to share in order to consume. Alice makes an offer x ∈ X = {0.01, 0.02,..., 0.98, 0.99}; and observing the offer, Bob accepts it or rejects it. If Bob accepts the offer, Alice gets 1-x and Bob gets x. If he rejects, then each gets 0.
(a) Compute all the subgame-perfect equilibria in pure strategies.
(b) Now suppose that their cousin Carol sells a contract for $0.01. The contract requires that Bob is to pay 1 dollar to Carol if Bob accepts an offer x that is less than X', where x'∈ X is chosen by Bob at the time of purchase of the contract. In particular, consider the following time-line:
• Bob decides whether to buy a contract from Carol and determines x' if he chooses to buy;
• Alice observes Bob's decision (i.e. whether he buys the contract and x' if he buys);
• Then, they play the bargaining game above, where Bob pays Carol 1 dollar if he accepts an offer x < x'.
Find all the subgame-perfect equilibria in pure strategies.
|
Implementing and supporting heterogeneous networks
: It is very common for corporations to support many types of network operating systems (NOSs). The most popular ones used are by Novell, Microsoft, Unix, Linux and Apple Macintosh. Explain in detail some major considerations and challenges when implem..
|
|
Provide a summary of each article
: In a 3- to 4-page paper, address the following points: Provide a summary of each article. Compare and contrast the strengths and weaknesses of each article
|
|
Provide a final set of documentation
: Provide a final set of documentation that includes a fully updated list of all services installed and describes all the standards that have been implemented on their systems. (This should essentially be an updated version of Lab #3 incorporating all ..
|
|
Maximize the selectivity for product
: The following sequences of reactions are to occur in a constant density reactor. Which type of continues flow-reactor would be best to maximize the selectivity for product C?
|
|
Compute the subgame perfect nash equilibriua in given game
: Compute the subgame perfect Nash equilibriua in the game below. Identify the path through the tree that each one represents, and the utilities of each player.
|
|
Percentage completion on profit-weighted-average method
: Gary Stevens and Mary James are production managers in the Consumer Electronics Division of General Electronics Company, which has several dozen plants scattered in locations throughout the world. What percentage completion would result in increasing..
|
|
Control of occupational hazards
: A specific hazard is identified for each workplace scenario. Identify one specific example of a control measure for each of the category of control strategy being asked
|
|
Activity driver for each activity cost category
: Calculate the cost per unit of activity driver for each activity cost category. Calculate the cost of Job 845 using ABC to assign the overhead costs. Calculate the cost of Job 845 using the plant wide overhead rate based on machine hours calculated i..
|
|
Forrest is given task of supervising their initial operation
: Forrest is the regional manager for a national chain of car rentals and is based in Washington, North Carolina. When the company opens new stores in Charlotte, Forrest is given the task of supervising their initial operation.
|