Reference no: EM131488323
CONTENTS (Answer Any 3 Questions)
1. Subnetting and Routing Protocols
Question 1 - Routing Protocols
a) Consider the following network. With the indicated link costs, use Dijkstra's shortest-path algorithm to compute the shortest path from x to all network nodes. Show how the algorithm works by computing a table.

b) Consider the three-node topology shown below. Let the link costs be c(x,y) = 3, c(y,z) = 6, c(z,x) = 4. Compute the distance tables after the initialization step and after each iteration of the distance-vector algorithm.
c) Consider the count-to-infinity problem in the distance vector routing. Will the count-to-infinity problem occur if we decrease the cost of a link? Why? How about if we connect two nodes which do not have a link?
Question 2 - IP Addressing
a) Consider a router that interconnects three subnets: Subnet 1, Subnet 2, and Subnet 3. Suppose all of the interfaces in each of these three subnets are required to have the prefix 223.1.17/24. Also suppose that Subnet 1 is required to support up to 63 interfaces, Subnet 2 is to support up to 95 interfaces, and Subnet 3 is to support up to 16 interfaces. Provide three network addresses (of the form a.b.c.d/x) that satisfy these constraints.
b) Consider a subnet with prefix 128.119.40.128/26. Give an example of one IP address (of form xxx.xxx.xxx.xxx) that can be assigned to this network. Suppose an ISP owns the block of addresses of the form 128.119.40.64/26. Suppose it wants to create four subnets from this block, with each block having the same number of IP addresses. What are the prefixes (of form a.b.c.d/x) for the four subnets?
c) Write a short note on IPv6.
Question 3 - IP routing Configuration
Scenario
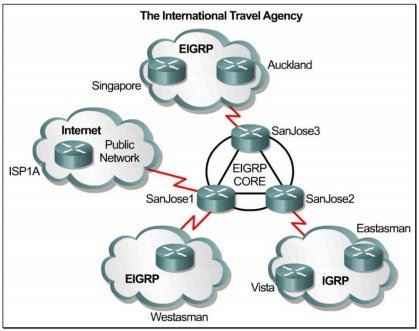
The responsibilities of the network engineer with International Travel Agency include creating and maintaining the San Jose campus network, connectivity to all regional headquarters, and Internet access via one or more service providers. The San Jose campus network must maintain 99.9% availability, while supporting 99% availability to regional headquarters. The network will be based on and must meet the following requirements:
1. The San Jose core routers must run EIGRP.
2. The network has been allocated one Class B license.
3. Use VLSM on all serial interfaces as may be appropriate.
4. This network will have three branches. The regional headquarters in Singapore and Auckland will run EIGRP. The Westasman branch office will run EIGRP. The Vista and Eastasman branch offices will run IGRP. (for configuring routing protocols correctly for different
5. Summarize all routes from each area into the core. Plan for approximately 30 networks in each area with exception of the core, which is exactly as shown in the diagram.
6. In the IGRP cloud of Vista and Eastasman, configure a DHCP server for a LAN segment. Use an IP helper address so that a workstation on another segment in that area can obtain an IP address from the DHCP server.
7. Configure Internet connectivity through a static route.
8. Document the configuration and any difficulties that were encountered.
9. What were the implementation issues or limitations?
10. List two suggestions for improving this network configuration and design.