Reference no: EM13380323
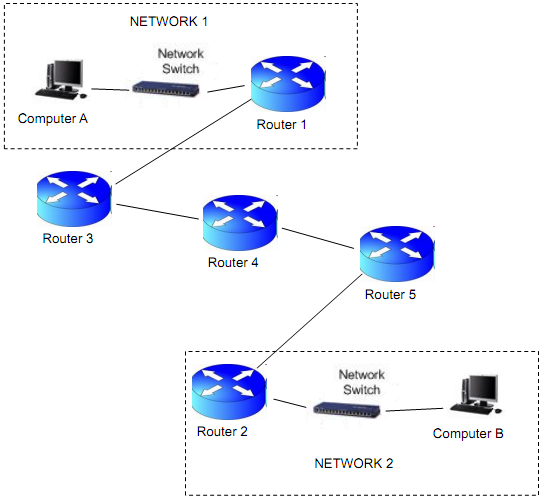
• An application on computer A (in network 1) is sending a message to an application on computer B (in network 2).
• There will also be a reply going back the other way.
• TCP is the transport layer protocol used for the messages and IP the network later protocol for the network.
• Ethernet is the datalink layer protocol for all the connections in the network.
• You can assume that computer A has obtained the destination port and IP address (probably from DNS)
• The above diagram shows the path taken by the messages as determined by the routing information held by the routers, etc.
• Network 1 is a class B network
• Network 2 is a small class C network
• Routers 3, and 5 belong ISPs with class B networks, and router 4 belongs to a top-level ISP with a class A network.
• Computer A is made by Spike technologies which has a MAC OUI of 45-FE-2A, computer B from Secombe technologies with an OUI of D2-34-C4, the routers are a mix of Trek Technologies with OUI 6B-3C-24 and Kirk Corporation with OUI 7F-9C-37
You are to:
1. Choose all the necessary and suitable MAC address, IP address for interfaces and port addresses implied by the above description. State clearly in your submission the choices you have made for these addresses.
Do not give the addresses in binary but in the X.X.X.X decimal format for the IP addresses, the hexadecimal format for MAC addresses and decimal numbers for the port numbers.
2. For the delivery of the message from Computer A to Computer B, for each step along the way show the source and destination
a. MAC addresses
b. IP addresses
c. Port addresses
Making it clear which is the source and which is the destination, in what packet or frame these addresses appear (IP, TCP, Ethernet) and what the order of encapsulation is.
3. The same as number 2, but for the reply from computer B to computer A
4. These messages are sensitive. What security vulnerabilities and threats can you see? What measures would you put in place to remove or minimize the vulnerabilities?