Reference no: EM13827923
1. Cryptography and Network Security: Principles and Practices, 6th Edition, by William Stalling,
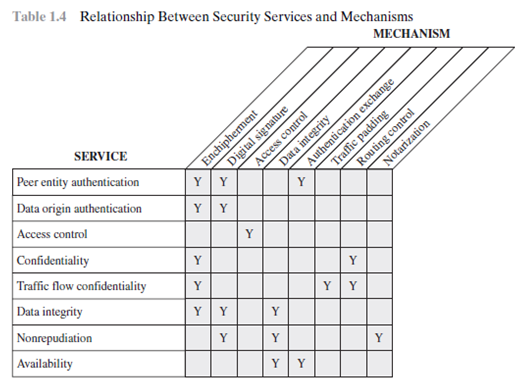
Draw a matrix similar to Table that shows the relationship between securityservices and attacks.
2. Chapter 2 of the textbook, Cryptography and Network Security: Principles and Practices, 6th Edition, by William Stalling.
1. What are the two basic functions used in encryption algorithms?
2. How many keys are required for two people to communicate via a cipher?
3. What is the difference between a block cipher and a stream cipher?
4. What are the two general approaches to attacking a cipher?
5. List and briefly define types of cryptanalytic attacks based on what is known to the attacker.
6. What is the difference between an unconditionally secure cipher and a computationally secure cipher?
7. Briefly define the Caesar cipher.
8. Briefly define the monoalphabetic cipher.
9. Briefly define the Playfair cipher.
10. What is the difference between a monoalphabetic cipher and a polyalphabetic cipher?
3
1. A ciphertext has been generated with an affine cipher. The most frequent letter of theciphertext is "B," and the second most frequent letter of the ciphertext is "U." Break this code.
2. Construct a Playfair matrix with the key largest.
b. Construct a Playfair matrix with the key occurrence. Make a reasonable assumption about how to treat redundant letters in the key.
3. Using the Vigenère cipher, encrypt the word "explanation" using the key leg.