Reference no: EM13923893
Question 1: What are the benefits of using a layered model for computer networks?
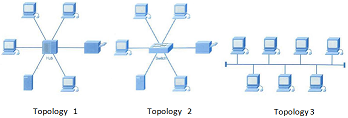
Question 2: The three network topologies shown below are all valid Ethernet networks.
a) How many collision domains and broadcast domains are there in each topology?
b) Explain which topology is preferred.
Question 3: Explain why 60.61.62.63/26 is not a valid host IP address.
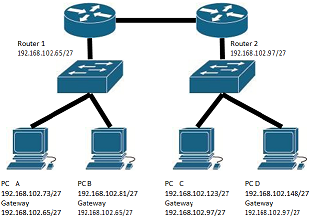
Question 4: In the following network topology, assume static routes are set and the routers are working properly. Explain why PC A can talk to PC C but PC B cannot talk to PC D.
Question 5: USQ has allocated 172.17.0.0/16 to 6 PC laboratories in Wonderland campus. Each laboratory will have a subnet of its own. The number of hosts in each laboratory is as follows:
|
|
Lab 1 Subnet A
|
Lab 2 Subnet B
|
Lab 3 Subnet C
|
Lab 4 Subnet D
|
Lab 5 Subnet E
|
Lab 6 Subnet F
|
|
Number of Hosts
|
2
|
47
|
532
|
6
|
39
|
125
|
The hosts in each laboratory are linked together using switches. The six laboratories are linked together using a router with six Ethernet interfaces as shown below. In the topology, only two hosts in each laboratory are shown. For each subnet, the gateway will use the first host IP address. The two PCs (for example, PC_B1 and PC_B2) in each subnet shown will be using the second available host IP address and the last available host IP address respectively.
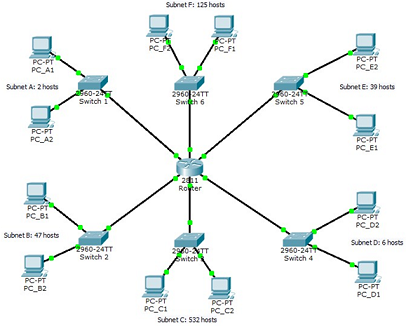
a) Taking into account of possible expansion of laboratory facilities in the future, we have to pack the subnets so that they use minimal IP address space. With this in mind, please assign IP addresses to the PCs and router Ethernet interfaces (gateways) using the table below:
|
Device
|
IP
|
Gateway
|
Broadcast IP
|
Subnet IP
|
|
PC_A1
|
|
|
|
|
|
PC_A2
|
|
|
PC_B1
|
|
|
|
|
|
PC_B2
|
|
|
PC_C1
|
|
|
|
|
|
PC_C2
|
|
|
PC_D1
|
|
|
|
|
|
PC_D2
|
|
|
PC_E1
|
|
|
|
|
|
PC_E2
|
|
|
PC_F1
|
|
|
|
|
|
PC_F2
|
|
b) Implement the network using Packet Tracer 6.0.1 subject to the following conditions:
1. Use one Cisco 2811 router with added Ethernet interfaces.
2. Use one Cisco 2960 24 port switch for each laboratory assuming other access switches can be added later on.
3. The router Ethernet interfaces use the first host IP address of the corresponding subnet assigned to the laboratory.
4. The two PCs shown in the topology should have the second available host IP address and the last available address of the subnet assigned.
c) When a TCP/IP packet travels from PC_A1 to PC_F1, we can capture the packets on their way using simulation mode. Use a Packet Tracer screen capture of the packets to explain where inside a packet/frame you can find:
1) Source MAC address and destination MAC address;
2) Source IP address and destination IP address.
|
Type of neuron that receives a stimulus
: Which of the following is a type of neuron that receives a stimulus and transmits it to the central nervous system?
|
|
Cordova leather liabilities
: 1. At December 31, 2014, Cordova Leather's liabilities include the following:
|
|
How would you define the target market of polaris products
: Identify and describe the strategies used in Polaris' marketing mix.With the Indian Motorcycle, specifically, what is the unique selling proposition (USP)?How would you define the target market of Polaris products?
|
|
The projects net present value
: Calculate the NPV for a 25 year project with an initial investment of 40000 and a cash inflow of 6000 per year. Assume that the firm has an opportunity cost of 18% . Comment on the acceptability of the project
|
|
Benefits of using a layered model for computer networks
: What are the benefits of using a layered model for computer networks? The three network topologies shown below are all valid Ethernet networks. How many collision domains and broadcast domains are there in each topology
|
|
Identify the beta listed for a company called elxsi?
: Identify the beta listed for a company called ELXSI, stock symbol ELXS. According to Yahoo!Finance, what is ELXI's beta?
|
|
Walmart analysis assignment
: Perform a vertical and horizontal analysis of Wal-Mart Stores, Inc.'s income statements and balance sheets as of January 31, 2015. In performing this analysis, consider any notable trends or changes that you observe that may provide useful informa..
|
|
What is the NPV break-even level of sales
: Modern Artifacts can produce keepsakes that will be sold for $70 each. Nondepreciation fixed costs are $2,300 per year, and variable costs are $35 per unit. The initial investment of $6,000 will be depreciated straight-line over its useful life of 5 ..
|
|
Journey from the testicles to the fallopian tubes
: The following is a list of methods by which human conception can be postponed. Which one blocks sperm on its journey from the testicles to the fallopian tubes?
|