Reference no: EM132219715
Network requirement analysis and plan
Purpose of the assessment (with ULO Mapping)
This assignment is designed to assess students' knowledge and skills related to the following learning outcomes:
a. Apply concepts and theories of human factors as related to network design and implementation;
b. Evaluate performance metrics and dimensions according to specifications.
Assignment Description
Project Scope: A typical network layout diagram of a medium sized firm is given below. Provided the advantages, the firm wants to redesign its network adapting a layered approach (core, distribution and access) in the design. The network design requirements are a) three layered network design (core, distribution and access) b) redundancy required in the core layer.
Gathering information about the existing network (such as IP addressing scheme, traffic restriction polices, applications used etc.) is paramount for any network redesign for seamless transition. In this regard, the staff members and IT staffs can be invaluable sources of information. A carefully designed questionnaire can be instrumental in gathering the information.
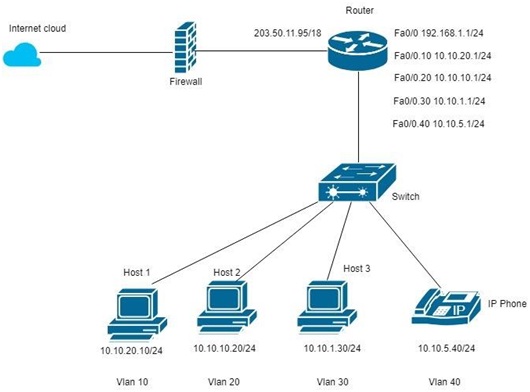
Figure. Network layout of a firm
Part I: Information collection
Develop a questionnaire to gather requirements from staff members, IT members and management.
The followings are to be covered in this section.
- What kinds of questions would you ask to better understand their environment to each group of users?
- For the Quality of Service (QoS) requirements, it is mandatory to acquire the information about the traffic types from the IT staffs and set the bandwidth requirement accordingly. Specifically, for the new design the followings criteria have to be satisfied.
For real time traffic, bandwidth percent should be set to 70 of the available bandwidth. For ftp traffic, bandwidth should be set is 200 kbps.
For SNMP traffic, bandwidth should be set to 800 kbps.
Note that the traffic information is important and will be used for QoS. QoS reflects on the performance evaluation of the design.
- How would you validate and verify the gathered information?
Part II: Network redesign and Demonstration
This is a network redesign and demonstration section. The following are to be covered.
- A three-layered network design (consisting of the Core, Distribution and Access) is needed.
- The new design must be the transformation of the existing design show in the figure above (i.e., IP addressing, number of departments etc., should remain intact in the new design).
For demonstration, the format would be a) no more than 2 persons in a group, b) at least 3 viva voce questions related to the design, and c) demo and viva voce duration 5 - 7 minutes (at max). The following is to be covered.
- Demonstration of a part of the design in Week 11 lab class (hardware platform)
Note to the lab tutor: As per the need, the lab tutor can allocate 15 minutes in Week 9 and Week 10 for work progression check and consultation.