Reference no: EM131428265
Question 1
(a) The primary function of a router is to determine the best path to use for sending packets. To determine the best path, the router searches its routing table for a network address that matches the destination IP address of the packet. Explain how the router processes an incoming packet using the routing table to determine the best path to forward the packet.
(b)
Figure - 1(b)
i. Identify the type of route used between the routers R1 and R2 that facilitates the router R2 to reach the four networks shown in Figure - 1(b).
ii. Explain how you will configure the routing between the routers R1 and R2.
iii. Justify your selection by discussing its advantages.
(c) As a network administrator, explain the specific circumstances where you would use a static default route for packet routing.
Question 2
(a) Discuss any FOUR (4) reasons for an occurrence of routing loop and its implications on a network operation.
(b) Using Bellman Ford algorithm, construct a topology database of the network for router - A as shown in Figure - 2(b) and include the entries that are selected for routing table.
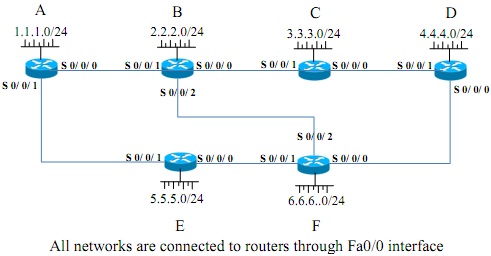
Figure - 2(b)
(c) One of the weaknesses of the Bellman Ford algorithm is that it does not have the capability to detect and eliminate routing loops.
i. With the aid of a diagram, explain how routing loops occur in Routing Information Protocol (RIP) enabled networks.
ii. Propose any TWO (2) methods which can be used to prevent the routing loops in the above said networks.
Question 3
(a) With the aid of a block diagram, analyse and describe how a router performs a hierarchical route lookup process when it receives an IP packet and decide which route in the routing table is the best match.
(b) Enhanced Interior Gateway Routing Protocol (EIGRP) has fast convergence time even though it is classified as Distance Vector Protocol. Explain the features of the EIGRP that reduces the time taken for convergence.
(c)
HQ# show ip route
<output omitted>
10.0.0.0/30 is subnetted, 1 subnets
C 10.10.10.252 is directly connected, Serial0/0/0
172.16.0.0/30 is subnetted, 1 subnets
C 172.16.100.0 is directly connected, Serial0/0/1
R 192.168.1.0/24 [120/1] via 10.10.10.254, 00:00:03, Serial0/0/0
R 192.168.2.0/24 [120/16] via 10.10.10.254, 00:00:03,
Serial0/0/0 R 192.168.3.0/24 [120/1] via 10.10.10.254, 00:00:03,
Serial0/0/0 R 192.168.7.0/24 [120/1] via 172.16.100.2, 00:00:04, Serial0/0/1
Figure - 3(c)
Analyze the output shown in the Figure - 3(c).
i. Explain why the network 192.168.2.0/24 is not reachable from the HQ router.
ii. Explain how the HQ router was informed by Routing Information Protocol (RIP) that the 192.168.2.0/24 is not reachable.
Question 4
(a)
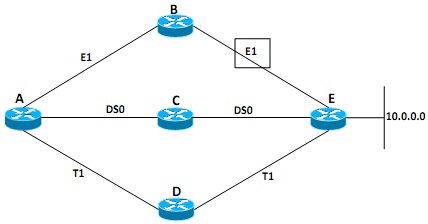
Figure - 4(a)
Calculate the best path to the network 10.0.0.0 from router-A in Figure - 4(a) using the Edsger Dijkstra's Shortest Path First (SPF) algorithm.
(b)
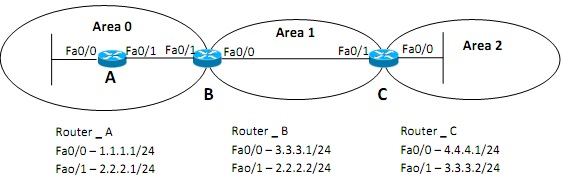
Figure - 4(b)
When designing Open Shortest Path First (OSPF) networks, all areas should be connected to the backbone area. However, due to topography constraint in Figure - 4(b) the Area-2 is connected with the Area-1. You are assigned to solve this problem.
i. Propose a solution to establish the connectivity for the Area-2.
ii. With the aid of diagram, explain your proposed solution.
iii. Provide the configuration of your proposed solution
(c)
Router# show ip eigrp topology
IP-EIGRP Topology Table for AS 1
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply, r - Reply status
<output omitted>
P 10.10.12.0/24, 1 successors, FD is 5514496
via 172.16.1.38 (5514496/28160), Serial0/1/0 via 172.16.1.42 (7693056/6172416), Serial0/1/1
<output omitted>
P 10.10.14.128/25, 1 successors, FD is 6026496
via 172.16.1.38 (6026496/2172416), Serial0/1/0 via 172.16.1.42 (7181056/28160), Serial0/1/1
<output omitted>
Figure - 4(c)
Analyze the output shown in the above Figure - 4(c)
i. Explain how the Diffusing Update Algorithm algorithm chooses the best path to the network 10.10.12.0/24 and 10.10.14.128/25.
ii. If the chosen path is suddenly down, explain what will happen.
Question 5
(a) The Figure - 5(a) shows the output for the "ip ospf neighbour" command.
|
Router#sh ip ospf neighbor .
|
|
Neighbor
|
ID
|
Pri State
|
Dead Time
|
Address
|
Interface
|
|
192.168.1.4
|
1
|
FULL/DR
|
00:00:38
|
192.168.1.4
|
FastEthernet0/0
|
|
192.168.1.2
|
1
|
FULL/DROTHER
|
00:00:31
|
192.168.1.2
|
FastEthernet0/0
|
|
192.168.1.1
|
1
|
FULL/DROTHER
|
00:00:32
|
192.168.1.1
|
FastEthernet0/0
|
Figure - 5(a)
i. Analyse the above adjacency table and draw the topology diagram with details.
ii. Evaluate the design implications of the topology you analysed in part (a).i.
(b) Analyse the output of the "show running-config" command shown in Figure - 5(b) and explain the characteristics of a protocol used to establish the communication between networks 192.168.1.0 and 192.168.2.0.
Router# show running-config
|
Interface
|
Subinterface
|
Gateway IP Address/Mask
|
VLAN
|
ID
|
Router Encapsulation
|
|
Fa0/0
|
fa0/0.10
|
192.168.1.1/24
|
10
|
|
dot1q 10
|
|
Fa0/0
|
fa0/0.20
|
192.168.2.1/24
|
20
|
|
dot1q 20
|
(c) Compare and contrast OSPFv2 and OSPFv3
Question 6
(a)
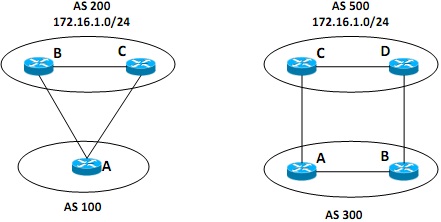
Figure - 6(a)
Figure - 6(a) shows two different scenarios for connecting Autonomous Systems (AS) using the Border Gateway Protocol (BGP). Explain how BGP path attributes are used to respectively set the preferred route as: AC from AS 100 to 200 and BD from AS 300 to AS 500.
(b) With the aid of a diagram, explain how the Internet Assigned Numbers Authority manages an IPv6 Global Unicast Address allocation to an organization.
(c) Discuss TWO (2) filter types that you can apply to the BGP update messages that your router exchanges with a particular BGP peer.