Reference no: EM13379911
1. Give an example to show that the group of permutations S5 is not commutative.
2. Use ECB mode with block length 3 and the permutation cipher for the following operation:
(a) Encrypt the plaintext 101100101111; key k = 
(b) Do the corresponding decryption.
To help with the next two questions, here are examples of block cipher encryption in CFB mode and in OFB mode. In both examples the block cipher, plaintext, and key are the same as in the examples for ECB and CBC modes that were presented in class.
Choose block length r = 3. The plaintext blocks are therefore m1 = 101, m2 = 100, m3 = 010, rn4 = 100, m5 = 101. As initialization vector, use IV = 1010. The CFB encryption is then shown in the left-hand table, and OFB encryption in the right-hand table:
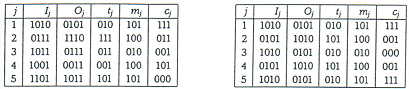
3. Encrypt the plaintext 100101110001 using (a) CFB mode and (b) OFB mode. Use the permutation cipher with block length 3, r = 2, and
key k =  . Use initialization vectors 000 in (a) and 010 in (b).
. Use initialization vectors 000 in (a) and 010 in (b).
4. Do the decryptions corresponding to 4(a) and 4(b).
5. Use the stream cipher discused in class, with n = 7 and c0 = c1 = 1, c2 = c3 = 0, c4 = c5 = c6 = 1. Encrypt w = 1110011 1110001 1010001 using the key k = 1010011.
6. (Nothing to be handed in). This may be the right time to familiarize yourself with the computer algebra system Maple. About how to download Maple. Our textbook (Trappe & Washington) has a very nice introduction in Appendix B, with instructions on how to download a special cryptography "notebook" for Maple. Do a few easy examples on the shift cipher and the affine cipher (pp. 498-499). Let me know of any problems you may have.
When we start using Maple in earnest in a few weeks, I will have to assume that everybody is familiar with the system.