Reference no: EM131017578
1. Tell two major differences between a VPN router and a VPN server (e.g., Cisco VPN concentrator).
2. Consider the remote access VPN scenario shown in the Figure. In this scenario, the remote user's PC is in a hotel room in LA, while the Corporate Office is in NYC. We assume that a program X executed by employee Alice in the LA hotel wants to send message "80 cents per share" to a server program Y executed on the Application Server (see Figure) in the Corporate Office.
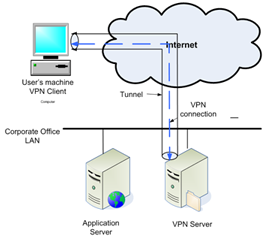
2.1 When the message leaves program X in the form of a packet, what is contained in the Destination IP field of the packet's header?
2.2 When the message leaves program X in the form of a packet, what is contained in the Destination Port field of the packet's header?
2.3 When the message leaves program X in the form of a packet, is the payload of the packet encrypted or not?
2.4 When the message leaves program X in the form of a packet, it will NOT instantly leave Alice's PC. Instead, it will be forwarded to another program Z. What is program Z?
2.5 After program Z gets the packet, what will program Z do against the packet?.
2.6 Before program Z sends out the revised packet, Z needs to let the VPN server (see Figure) authenticate Alice. For this purpose, program Z will send information W to the VPN server. What is info W?
2.7 After the VPN server receives info W, the VPN server will forward W to another server T. What is the name of server T?
2.8 After the VPN server receives a positive reply from server T, the VPN server will tell program Z that Alice is a legitimate employee. Then program Z will send out the message to the VPN server. When the message leaves program Z, what is contained in the Destination IP field of the packet's header?
2.9 When the message leaves program Z, what is contained in the payload of the packet?
2.10 After a while, the message will arrive at the VPN server. When the message arrives at the VPN server, how will the packet be handled by the VPN server? Please give a step-by-step description
2.11 After a while, the VPN server will want to forward the message to the Application Server (see Figure). Why does the VPN server not want to forward the message to server T? (
2.12 When the message leaves the VPN server, what is contained in the Source IP field of the packet?
2.13 During the whole process, how many times has the message been encrypted?
2.14 During the whole process, how many times has the message been decrypted?
|
Write an essay proposal for african music history
: Write an essay proposal for African Music History. The desscription of African music. Described the earlist Africa music and how does it start. How did the music change in these years?
|
|
What are the most important aspects of the site
: What makes this site so historic and what are the most important aspects of the site? Your impressions of the site: what were you most impressed by, were you surprised by what you learned, etc.
|
|
Write a program for ijvm called scramble
: Write a program for IJVM called scramble that takes lowercase text from input and prints the next character (i.e. ‘b' is printed as ‘c') and uppercase text and prints the character before (‘B' is printed as ‘A'). Print all other characters as is.
|
|
Compare the tax advantages of debt versus equity capital
: Use the Internet and Strayer databases to research the advantages and disadvantages of debt for capital formation versus equity for capital formation of a corporation. Prepare a formal letter to the client using the six (6) step tax research proce..
|
|
What is contained in the payload of the packet
: After the VPN server receives a positive reply from server T, the VPN server will tell program Z that Alice is a legitimate employee. Then program Z will send out the message to the VPN server. When the message leaves program Z, what is contained ..
|
|
Professional judgment in context feature
: Inherent risk at the financial statement level relates to (a) business and operating-related risks and (b) financial reporting risks.The Professional Judgment in Context feature, "Risks Associated with Financial Statement Misstatements,
|
|
Crossing over occurs during which phase of meiosis
: ATP is generated by both plants and animals using ATP synthase and a proton gradient.
|
|
Estimate the fixed cost of electricity per month
: Using the high-low method, estimate the fixed cost of electricity per month and the variable cost of electricity per occupancy-day. Round off the fixed cost to the nearest whole dollar and the variable cost to the nearest whole cent.
|
|
Find the equation in y-intercept form for this given line
: You are told that the point (X, Y) = (10, 20) sits on a straight line. You are also told that this line intersects the X-axis at 30. Given this information, find the equation in Y-intercept form for this line. Show your work for full credit
|