Reference no: EM131212741
For each of the schedules of transactions T1, T2, and T3 below:
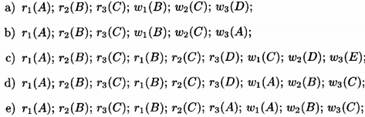
do each of the following:
i. Insert shared and exclusive locks, and insert unlock actions. Place a shared lock immediately in front of each read action that is not followed by a write action of the same element by the same transaction. Place an exclusive lock in front of every other read or write action. Place the necessary unlocks at the end of every transaction.
ii. Tell what happens when each schedule is run by a scheduler that supports shared and exclusive locks.
iii. Insert shared and exclusive locks in a way that allows upgrading. Place a shared lock in front of every read, an exclusive lock in front of every write, and place the necessary unlocks at the ends of the transactions.
iv. Tell what happens when each schedule from (iii) is run by a scheduler that supports shared locks, exclusive locks, and upgrading.
v. Insert shared, exclusive, and update locks, along with unlock actions. Place a shared lock in front of every read action that is not going to be upgraded, place an update lock in front of every read action that will be upgraded, and place an exclusive lock in front of every write action. Place unlocks at the ends of transactions, as usual.
vi. Tell what happens when each schedule from (v) is run by a scheduler that supports shared, exclusive, and update locks.
|
Determining the best practices
: Create a list of three best practices recruiters should use when screening potential candidates for a HR management position. Justify your selections.
|
|
Conflicts of interest arise in all organizations
: Conflicts of interest arise in all organizations. This module shows that no organization, whether public or private, is exempt from issues related to conflicts of interest.
|
|
Write one log record to disk while a previous record
: You may assume that log records are written to disk in the order shown; i.e., it is not possible to write one log record to disk while a previous record is not written to disk.
|
|
Should government of indonesia block export of jelutong wood
: What should be done about the use of jelutong wood in making pencils? - Should the government of Indonesia block the export of jelutong wood?
|
|
What happens when each schedule is run by a scheduler
: Tell what happens when each schedule from (iii) is run by a scheduler that supports shared locks, exclusive locks, and upgrading.
|
|
Declare a two-dimensional array
: Declare a two-dimensional array that contains 10 rows , each of which will store 4 doubles. Eexecute the program in C++ explain how the array is initialized, how it is used in the program, how the nested for loops work, and what the output of the p..
|
|
Identify historical events that led to the implementation
: Identify historical events that led to the implementation of current standards. Analyze how these events and standards are correlated and the impact that they have on the accounting profession in Germany today.
|
|
How many interleavings of transactions are serializable
: If the order of incrementation in T2 were reversed [i.e., inc2 (B) followed by inc2 {A)], how many serializable interleavings would there be?
|
|
Judicial precedents set by earlier decisions
: Why do courts generally adhere to the judicial precedents set by earlier decisions?
|