Reference no: EM133333
QUESTION 1
Broadly sort and discuss the types of safekeeping that exists in communications?
QUESTION 2
a) Briefly confer the 3G Safekeeping model.
b) What are the main disparities between the 3G and GSM safekeeping models.
c) Interception within a 3G network can be quite problematic, as we know it. Regardless of that it is important to know how interception happens in such a network. Discuss about the concept and how this is attained.
d) In relation to interception on a 3G network what can be done to secure such hole in the organization.
QUESTION 3
Mobile wireless networks have transformed enterprises and generally how we communicate, freeing end-users from ties to a desktop computing setup and allowing them to be far more productive. A truly mobile network would have a significant advantage with the flexibility to shift strategies and being more competitive.
However, what's been missing from the idea of a mobile enterprise is a method to substantively evaluate the end-to-end safekeeping of such networks. There has been no truly reasonable way to accurately review every safekeeping aspect of a network and provide IT professionals with solutions that identify and correct safekeeping shortfalls.
You are hired as a safety Expert to provide a framework, which would be based around the foundation for safekeeping architecture standards ITU-T X.805 and ISO/IEC 18028-2, which tenders a result to this problem. The framework as we know should deliver a comprehensive methodology for assessing and upgrading end-to-end network safekeeping across the network. You will be playing a big role in helping bring secure connectivity to enterprises and government agencies with an understanding that to be truly effective, end-to-end safekeeping considerations must be evaluated and properly implemented at every stage of a network's lifecycle.
Admittedly, performing a inclusive safekeeping evaluation is a complex undertaking. Your sanctuary Framework should make it possible to evaluate one of the most vulnerable aspects of any infrastructure - in this case mobile - which is the air link. Furthermore, IT professionals should be able to determine if data travelling across that link is passably defended and, if not, what steps to take to assist in rectifying the situation.
The Reference Architecture
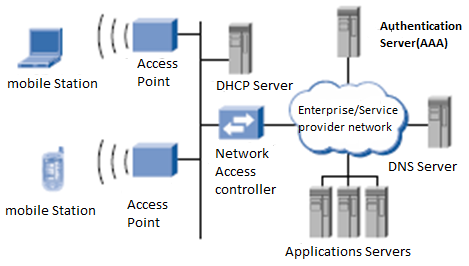
The orientation architecture for this assessment is based on a typical Wi-Fi network used by enterprises and hot spot service providers and includes a set of access points (AP), network admission controller (NAC) and authentication server (AS) as shown in stature 1.
The AP supplies wireless access to laptops, PDAs (personal digital assistants), and other mobile stations. It also supplies these devices with in sequence about the WLAN and responds to demand from them.
The main purpose of the Network Access Controller (NAC), commonly referred to as a "WLAN Gateway," is to perform or assist with user confirmation and to control network access. The NAC will not permit access to the network behind it unless the mobile station has been successfully authenticated and sanctioned.The NAC may put together other functions, including NAT (network address translation), DHCP (dynamic host configuration protocol) server, authentication server, and VPN server, etc.
The confirmation server is critical to implementing advanced safekeeping criterions such as 802.1x, WPA, and 802.11i/Robust Secure Network (RSN). It is responsible for user verification and authorization and can optionally participate in the key management. The remaining factors shown in the position architecture are common to wireless and wired networks.
Scope of the examination
The scope of the safekeeping analysis will include the end- to-end Wi-Fi network architecture and the entire framework from the ITU-T X805 should be functional, vulnerabilities should be identified for every layer, plane and dimension. For the sake of simplicity, the scope of analysis in your reacts should be limited to wireless admittance only. All applications running on top of Wi-Fi access with other enabler services such as DNS, DHCP, AAA etc., should be ruled out from the scope of your analysis.
a) Every type of Wi-Fi attack poses one or more threats, depending on intent and approach. Map down five popular Wi-Fi attacks to the threat model based on the ITU-T X805 Safekeeping Framework.
b) Scrutinize the impact on WIFI Layers.
c) Scrutinize the impact on the WIFI Planes.
d) Briefly illustrate the 8 safekeeping dimensions
e) Consider the effectiveness or the sufficiency of the controls available in each of the eight dimensions for all applicable modules in an attempt to determine the relative potency and weak spots of 802.11i, WPA2, WPA and WEP safekeeping standards.
|
Tourism organisations to carry out marketing research
: Explain why is it important for tourism organisations to carry out marketing research Explain how you would carry out an effective interview
|
|
Digital stratigraphy
: concept of Message Digest, File Carving, MD5, Locard's Exchange, Parker's categories, computer-related crime as suggested by Donn Parker, computer systems as sources of digital evidence
|
|
Identify and explain one type of market segmentation
: Identify and explain one type of market segmentation that you believe is being adopted by the Virgin Group Describe two other types of market segmentation that can be adopted by Virgin Group and explain the importance of market segmentation, tar..
|
|
Explain the marketing concept
: Discuss four types of market segmentation. Provide examples to support your answer Explain the marketing concept
|
|
Mobile wireless networks
: 3G Safekeeping model, safekeeping architecture standards ITU-T X.805 and ISO/IEC 18028-2, access points (AP), network admission controller (NAC) and authentication server (AS)
|
|
Critically examine the scope of marketing analysis
: Critically examine the scope of Marketing Analysis that a company needs to undertake in the development of a Marketing Strategy (b) The effectiveness of a Marketing Plan is dependent on segmenting, targeting, differentiation and positioning proce..
|
|
The different bases of market segmentation
: The stages of the product life cycle The promotional mixes The different bases of market segmentation
|
|
What is customer relationship management
: What is Customer Relationship Management and Give two major differences between CRM and eCRM
|
|
Encryption and hashing
: securing a new web server and a new web application, input validation, CSRF attack, SQL injection vulnerability, Cross Site Scripting (XSS) attack, architecture mechanism Linux, Apache, MySQL, and PHP,
|