Reference no: EM131215070
There are a number of other notions of edit distance available. For instance, we can allow, in addition to insertions and deletions, the following operations:
i. Mutation, where one symbol is replaced by another symbol. Note that a mutation can always be performed by an insertion followed by a deletion, but if we allow mutations, then this change counts for only 1, not 2, when computing the edit distance.
ii. Transposition, where two adjacent symbols have their positions swapped. Like a mutation, we can simulate a transposition by one insertion followed by one deletion, but here we count only 1 for these two steps.
Repeat Exercise 3.5.7 if edit distance is defined to be the number of insertions, deletions, mutations, and transpositions needed to transform one string into another.
Exercise 3.5.7
Find the edit distances (using only insertions and deletions) between the following pairs of strings.
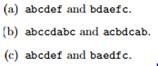
|
Find the pmf of the random variable y
: In terms of PX (k ), find the PMF of the random variable Y if its probability-generating function is given as in each of the following cases.
|
|
Why is programming efficiency important
: Taking into account the availability of today's powerful computers, why is programming efficiency important? Consider how the number of lines of programming instructions impact the number of CPU processing cycles?
|
|
Moment generating function of a rayleigh random variable
: Derive an expression for the moment-generating function of a Rayleigh random variable whose PDF is:
|
|
Provide your own short java code example
: Instructions for HW: Provide your own short Java code example that uses a For or While loop. Be sure to test and describe what your code is doing.
|
|
Find the edit distances between the following pairs
: Mutation, where one symbol is replaced by another symbol. Note that a mutation can always be performed by an insertion followed by a deletion, but if we allow mutations, then this change counts for only 1, not 2, when computing the edit distance.
|
|
Rician random variable with a pdf
: Derive an expression for Note that this is not quite the moment-generating function, but it can be used in a similar way.
|
|
Why it is important to learn how to implement data structure
: Discuss why it is important to learn how to implement data structures, even though the STL is available. Identify advantages of knowing data structures in detail.
|
|
Define role of personality in affecting situational behavior
: Examine the personality characteristics attributed to each theory in your approach. Explain the interpersonal relational aspects associated with the theories selected. Include a reference page with a minimum of three to five peer-reviewed sources.
|
|
Find the mean of the gaussian mixture
: Find the moment-generating function, MX(u) , of the Gaussian mixture. - Use the moment-generating function to find the mean of the Gaussian mixture.
|