Reference no: EM131371308
1. Develop the function reachable. It consumes a node in a simple graph. Its effect is to place true into the visited fields of all those nodes that are reachable from the given node and to ensure that the visited fields of all other nodes are false.
2. Develop make-simple-graph, a function that manages the state of a locally defined graph. The function accepts a simple graph in the form of lists of pairs of symbols: (list of (list symbol symbol)). It supports four services:
1. adding nodes that are connected to already existing nodes (by name);
2. changing the connection of a node (by name);
3. determining whether a route between two nodes exists;
4. and removing nodes that are not reachable from some given node.
Hint: Instead of using a list, the manager should use a node sequence, which is analogous to the hand structure from section
41.3. A node sequence relies on the following structure:
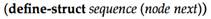
A sequence is similar to a list, but it supports structure mutations.
|
Order is based on economic order quantity
: The annual demand for an office supply company is 24,000 units. Its costs $30.00 to place an order and the holding cost per unit per year is $1.75. The company places an order on a quarterly basis. How much company will save its annual inventory cost..
|
|
Discuss about the antecedents of target marketing
: Assumes that all members of a market have similar needs that can be met with a single marketing mix. A concentrated targeting strategy focuses all marketing efforts on a single market segment. Multi-segment targeting is a strategy that uses two or..
|
|
Middle-class neighborhoods
: 1) You are interested in finding out if Obama's health care policies have resulted in a greater increase in blood pressure screenings in poor neighborhoods than those in middle-class neighborhoods. Which of the following would best describe the ty..
|
|
Write a resume or cover letter for campus attendant job
: Write a resume or cover letter for Campus attendant job at University of Houston.- Provide excellent customer service to students dropping off and picking up laundry at the truck at Houston.
|
|
Determining whether a route between two nodes exists
: Develop the function reachable. It consumes a node in a simple graph. Its effect is to place true into the visited fields of all those nodes that are reachable from the given node and to ensure that the visited fields of all other nodes are false.
|
|
Diploid parent sporophyte cells and diploid recombinant
: Describe the genetic/genealogical relationship between diploid parent sporophyte cells and diploid recombinant offspring sporophyte cells?
|
|
Example to concepts of biotic integrity
: Are animals in zoos or aquariums better off than their counterparts in the wild? Why or why not? Choose an animal species and discuss relative levels of competition, parasites, disease loads, predation threats, animal psychology, and social relati..
|
|
Evaluation of the internal critical success factors
: Undertake a critical evaluation of the internal Critical Success Factors (CSF's) that can determine success/failure in your chosen organisation's Market Development planning. 'How' the organisation needs to strategically plan its international Rel..
|
|
Endangered plant or animal species from the region
: What is an endangered plant or animal species from the region where you live? How would you describe the effective population size of that species? What is the relationship between population size, genetic vigor, and conservation practices for thi..
|