Reference no: EM131219955
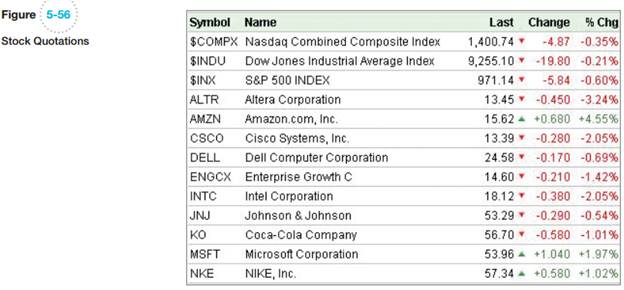
Examine the list of stock quotes in Figure 5-56. Using the structure and example data items in this list, do the following:
A. Create a single-entity data model for this list. Specify the identifier and attributes.
B. Modify your answer to A to include the entities COMPANY and INDEX. Specify the identifier and attributes of the entities and the type and cardinalities of the relationships. Explain which cardinalities can be inferred from Figure 5-56 and which need to be checked out with users.
C. The list in Figure 5-56 is for a quote on a particular day at a particular time of day. Suppose that the list were changed to show closing daily prices for each of these stocks and that it includes a new column: Quote Date. Modify your model in B to reflect this change.
D. Change your model in C to include the tracking of a portfolio. Assume the portfolio has an owner name, a phone number, an e-mail address, and a list of stocks held. The list includes the identity of the stock and the number of shares held. Specify all additional entities, their identifiers and attributes, and the type and cardinality of all relationships.
E. Change your answer to part D to keep track of portfolio stock purchases and sales in a portfolio. Specify entities, their identifiers and attributes, and the type and cardinality of all relationships.
|
How management can prevent unethical behavior from happening
: Your talk should include a description of three (3) types of ethical dilemmas that could happen in the workplace and the potential impact of each dilemma on the following: 1) the organization, 2) employees and, 3) stakeholders. Discuss how managem..
|
|
Key factors for future competitive success
: Discuss with your class the key factors for future competitive success. List the common types of key success factors and answer the following questions:
|
|
Outlier payment calculation to determine
: The Safe-Cross® guidewire is present on the following claim. Complete an outlier payment calculation to determine whether this claim would qualify for a high cost outlier payment.
|
|
Identify relevant thesis statement or question from article
: HC1052 Individual Assignment. Write an article critique of 1,500 words. The Article Critique that you write must: Identify a relevant Thesis Statement or Question from the article and Identify the strengths and weaknesses of the article based on the ..
|
|
Create a single-entity data model for this list
: The list in Figure 5-56 is for a quote on a particular day at a particular time of day. Suppose that the list were changed to show closing daily prices for each of these stocks and that it includes a new column: Quote Date. Modify your model in B ..
|
|
Production with respect to direct materials-conversion
: Victory Company uses weighted-average process costing to account for its production costs. Conversion cost is added evenly throughout the process. Direct materials are added at the beginning of the process. Determine the equivalent units of productio..
|
|
Command the obedience of followers
: One classification of leaders is those who command the obedience of their followers. Others utilize their position to improve themselves, gaining enriching experiences, sometimes at the frustration of those they lead.
|
|
Explain how metrics are used to evaluate the success
: Create an MS PowerPoint Presentation - define the term metrics, explain how metrics are used to evaluate the success of the total rewards program, identify, describe, and provide examples of at least three metrics and share how you will collect th..
|
|
Guidelines for performing project management functions
: Why is it important to have standards or guidelines for performing project management functions?
|