Reference no: EM131109256
Performance Models of Computers and Networks
In this project, you will need to use discrete event simulation approach I introduced in class to simulate the traditional "machine-repairman" closed queuing network.Please check "examples" lecture notes (lecture 13) Page 2-5 for the machine-repairman problem description.
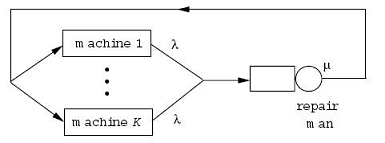
Assume that there are c=3 machines, failing rate 0.2 /min, the repair rate 0.5 /min. That is to way,
each machine works for an exponential distributed time with rate 0.2 /min before it fails, and the repairmen takes an exponential distributed time with rate 0.5 /min to finish repairing a failed machine. If there are more
than one failed machines, the repairman uses “first come, first serve” to repair failed machines. For discrete event simulation, define system state N(t) as the number of working machines at time t.
You need to simulate this system until the repairman has finished repairing 100 machines. Please use C or C++ or Java to write this simulation code. Write simulation output into a “data.txt” file and then use Matlab .m code to read the data and process the data. Your Matlab data processing code should provide results of:
(1). The steady state probability for all states based on your simulation result.
(2). The utilization rate of the repairman, i.e., =P(repairman busy) based on simulation result.
(3). The average number of working machines based on your simulation result
4). The analytical results of steady state probabilities, utilization rate, and average number of working machines. Calculate the corresponding theoretical solutions based on lecture notes Page 2-5. Compare your theoretical solutions with the simulation results for steady state probabilities in above (1) in the format of one figure (with two curves), for the above (2) to (3) by listing their values side-by-side in a table. If they differ too much, either your
analysis or simulation code must have something wrong.
Repeat the simulation again until the repairman finished repairing 10,000 machines. Based on your simulation results, plot the comparison figure between simulation result and analytical result, and answer the above question (2) to (3) again and also put their results in the comparison table.
Submission: please submit a project report with explanations of your design, codes, figure result and table result. In addition, submit your program source code (include the simulation C/java code and Matlab .m code) and the first 100 machine repairing simulation output “data.txt” file. Please zip all these files together to submit via webcourse.
In your report, you need to explain:
(1). What important variables you use (such as counters and system state)?
(2). What events do you define? What is included in the event list?
(3). What is your simulation code (C or java code) output and output file format?
(4). The variables you used in your simulation code and Matlab code correspond to what?
Note: In my lecture, I have introduced semi-simulation based on Markov model and realistic simulation. For this project, you need to conduct realistic simulation, i.e., you need to simulate each machine’s status change. For example, if we use (0,1,1) to represent machine #1 is not working, machine #2 and #3 are working, then the state “2” in examples.pdf lecture note (Page 3) includes three possible system states in simulation: (0,1,1), (1,0,1), and (1,1,0). In other works, you need to map your simulation states into the states defined in the analysis in lecture notes in order to make comparison.
If you cannot make your realistic simulation work but can simulate based on Markov model, then you will have 15 points off.