Reference no: EM131428240
Question 1
(a)
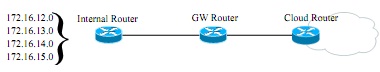
Figure - 1(a)
Analyse the topology shown in Figure - 1(a) and choose and explain the appropriate routing techniques that are able to provide optimum performance to connect the GW- Router to a private cloud for both outbound and inbound traffic. In addition, provide the configuration for your chosen techniques.
(b)

|
|
John - PC
|
Router - A
|
Router - B
|
Alex - PC
|
|
IP address
|
1.1.1.1/24
|
Fa0/0 - 1.1.1.254/24 Fa 0/1 -192.168.1.1/30
|
Fa0/0 -2.1.1.254/24 Fa0/1 -192.168.1.2/30
|
2.1.1.1/24
|
|
Mac Address
|
1111.1111. 1111
|
Fa0/0 - 2222.2222.2222
Fa0/1 - 3333.3333.3333
|
4444.4444.4444
5555.5555.5555
|
aaaa.aaaa.aaa a
|
Figure - 1(b)
Describe step-by-step the procedure of the routing process that takes place when user John sends a packet to user Alex.
(c) As a network administrator, explain any FIVE (5) reasons to justify the choice of recommending the Link State Protocol (LSP) for a given network scenario.
Question 2
(a) Using Bellman Ford algorithm, construct a routing table for router - B as shown in Figure - 2(a).
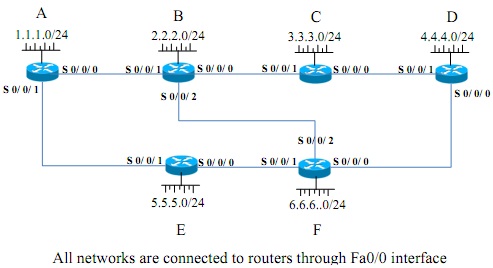
Figure 2(a)
Use Table-2(a) to create the routing table.
|
Network
|
Exit interface
|
Next Hop Address
|
Hop Count
|
Administrative Distance
|
Table-2(a)
(b) Analyze and assess the consequence when a second topology change emerges before a network is able to converge on the first change in a network which uses Routing Information Protocol (RIP). Use diagrams to support your explanation.
(c) Provide TWO (2) types of IPv6 address representations with appropriate justification.
Section - B
Answer ANY TWO (2) of the THREE (3) questions in this section. All questions carry equal marks.
Question 3
(a) You have been assigned to manage a part of an enterprise network as shown in Figure - 3(a) and found that the network performance is poor due to the heavy broadcast from a large number of users. Your organization's budget does not allow you to upgrade or purchase any additional hardware.
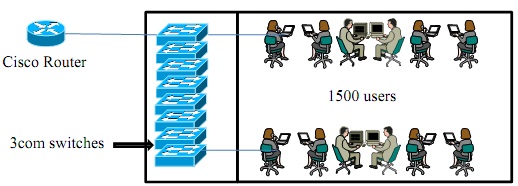
Figure - 3(a)
i. Propose an appropriate solution to improve the performance of the network and justify your chosen technique.
ii. Explain other benefits of your proposed solution.
(b) Assess the impact of your proposed solution for question - 3(a) on the router configuration and suggest the details of changes of configuration that are required to enhance seamless communication between users from all the VLANs.
(c)
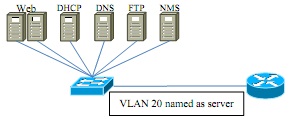
Figure - 3(c)
You have been assigned to improve the performance access time of servers of your organization located in the server farm as shown in Figure - 3(c). When analyzing the traffic flow of VLAN configured for all servers, you have found that the performance degradation is due to broadcast messages associated with the DHCP and DNS servers. Provide an appropriate solution to solve this problem and with the aid of a diagram, explain its architecture.
Question 4
(a)
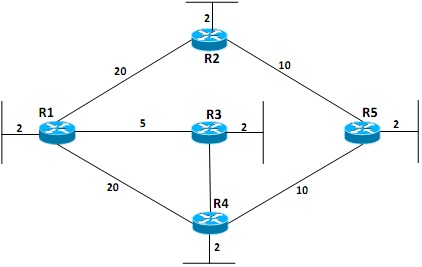
Figure - 4(a)
Figure 4(a) shows the topology with each link cost. Construct the Shortest Path First (SPF) routing table for the router R1 using the Edsger Dijkstra's algorithm.
(b)
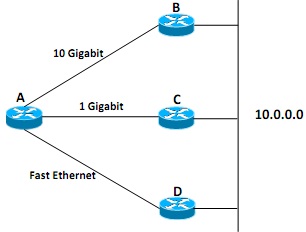
Figure - 4(b)
All routers shown in Figure 4(b) are enabled with Open Shortest Path First (OSPF) with default settings. Router-A learns of the network 10.0.0.0 via routers B, C and D.
i. Analyze and explain the problems involved in building a routing table to route packets from router-A to the network 10.0.0.0.
ii. Propose your solution to solve the problems and explain the result of your proposed solution.
(c)
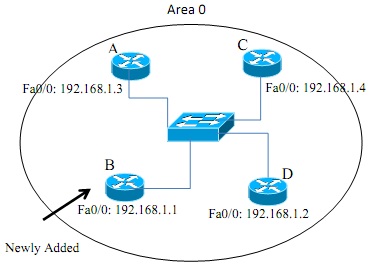
Figure - 4(c)
You are assigned to install and configure the new higher version router with OSPF in your organization. Evaluate the OSPF behavior in the topology shown in Figure - 4(c) and propose your configuration design with justification.
Question 5
(a)
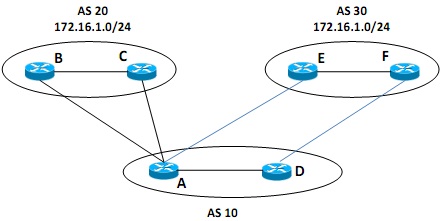
Figure - 5(a)
Figure - 5(a) shows two different scenarios of connecting Autonomous Systems (AS) using Border Gateway Protocol (BGP). Explain how BGP path attributes are used to set the preferred route as AC from Autonomous System (AS) 10 to 20 and the preferred route as DF from AS 10 to AS 30.
(b)
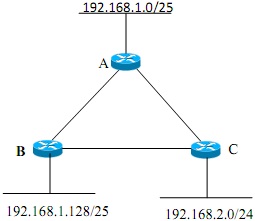
Figure - 5(b)
You have been assigned to troubleshoot the network shown in Figure - 5(b) which was configured by a trainee engineer with RIP version-1. The network 192.168.2.0 is able to ping from the other two networks, but failed to ping from 192.168.2.0 is failed. Evaluate the existing RIP configuration and provide a solution to your trainee.
(c) Compare and contrast Open Shortest Path First version-2 and version-3 operation.
|
Summarize the article-the debate over doing good
: Summarize the Grow, Hamm, & Lee's "The Debate over Doing Good" (below).Research a community organization(each one teach one), their community partners and the way they use volunteers.Select 6 separate articles and Review each of the six articles you..
|
|
Times the value of the dimes
: A piggy bank contains 53 coins, all of them nickels, dimes, or quarters. The total value of the coins is $4.75, and the value of the quarters is two times the value of the dimes. How many coins of each type are there?
|
|
Circulation of the paper
: It is estimated that the annual advertising revenue received by a certain newspaper will beR(x) = 0.5x2+ 3x+ 160 thousand dollars when its circulation isxthousand. The circulation of the paper is currently10,000and is increasing at a rate of3,000pe..
|
|
Extreme values of the function subject
: This extreme value problem has a solution with both a maximum value and a minimum value. Use Lagrange multipliers to find the extreme values of the function subject to the given constraint.f(x,y) =8x+8y; x2+y2=32.
|
|
Describe step-by-step the procedure of the routing process
: Analyze and assess the consequence when a second topology change emerges before a network is able to converge on the first change in a network which uses Routing Information Protocol (RIP). Use diagrams to support your explanation
|
|
What examples of learning by happy accident
: What examples of learning by "happy accident" or just by chance have you experienced in your own life? What do you think it means for a person (especially a scientist) to have a "prepared mind," as Pasteur describes
|
|
Which of the below behaviors are inappropriate in a course
: Which of the below behaviors are inappropriate in a course? Posting in the course's threaded discussions is an essential element in our online, asynchronous classroom. Which of the following is not an example of value-adding posting?Choose from the..
|
|
Hale hardware takes pride as the shop around the corner
: Hale Hardware takes pride as the “shop around the corner” that can compete with the big-box home improvement stores by providing good service from knowledgeable sales associates (many of whom are retired local handymen). How much additional sales re..
|
|
What are the types of business entities
: Josh Smith is an engineering student at CBU. He has contacted you regarding a product idea. He has an idea for a software program and sensor to alert a driver if a child is left in a car. He knows that you have knowledge about the law because you tak..
|