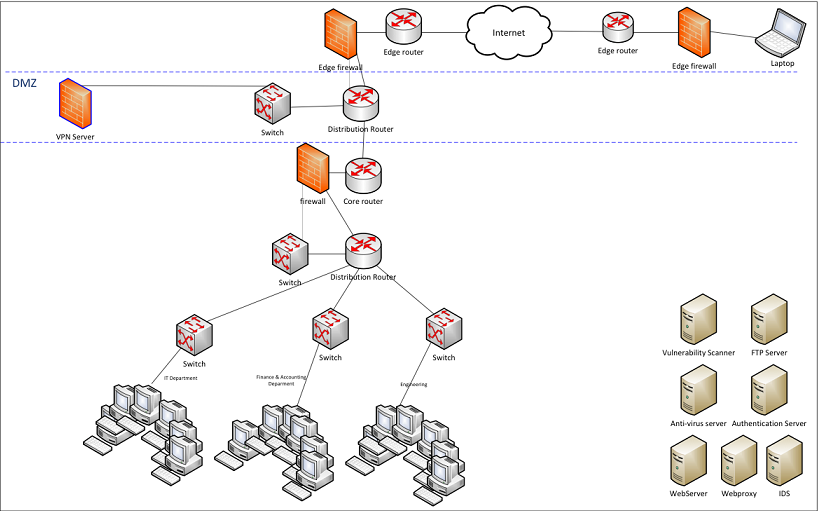
Reference no: EM13754968
Using the network diagram below, your task is to incorporate the devices on the lower right into the diagram to create a secure corporate network. The devices you need to incorporate into the network diagram include: Web server, ftp server, vulnerability scanner, anti-virus server (client-based / server-based), Web proxy, intrusion detection system (IDS), and authentication server.
Write a four to five (4-5) page paper in which you:
Determine which devices you will use for both the current network diagram infrastructure consisting of firewalls, routers, and workstations as well as the device you need to incorporate. Include the following for each:
Make or vendor's name (e.g., Microsoft, Redhat, Cisco, Juniper, Netgear, 3Com, etc.)
Model (e.g., Windows 7, ASA 5500, Cisco 3500, Squid, etc.)
IP address assigned to all devices
Establish the configuration for each device in which you:
Research each of the devices you chose and provide a basic configuration you would use in your network.
Use IP addresses to describe your configuration.
Explain the impact that each of your configurations has on the security of the entire network.
Highlight at least five (5) security features for each device, including devices in network diagram.
Using Microsoft Visio or its open source alternative to create a final network diagram that incorporates all devices into the existing network and ensures the following:
VPN sessions (from laptop) are only allowed to access the desktops in the IT department by IT department employees.
All VPN connections from the Internet cloud into the corporate network terminate at the VPN server.
Users from Engineering and Finance and Accounting CANNOT communicate.
Vulnerability scans occur daily in which all desktops are scanned at least once per day.
Use at least three (3) quality resources in this assignment. Note: Wikipedia and similar Websites do not qualify as quality resources.