A very useful application of assembly is to generate delay loops. These loops are used for waiting for some time before execution of subsequent instruction.
However how to find time for the delay? The rate at which instructions are executed is determined by clock frequency. Every instruction occupies a certain number of clock cycles to execute. This multiplied by clock frequency of microprocessor gives actual time of execution of an instruction. For illustration MOV instruction occupies four clock cycles. This instruction when run on a microprocessor with a 4 MHz clock occupies 4/4 which means 1 microsecond. NOP is an instruction which is used to produce the delay without affecting actual running of program.
Time-delay of 1 ms on a microprocessor having a clock frequency of 5 MHz will necessitate:
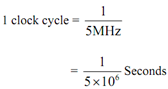
Thus, a 1-millisecond delay will require:
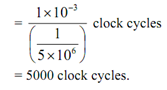
The subsequent program section can be used to produce the delay with counter value correctly initialised.
MOV CX, N ; 4 clock cycles N will vary depending on
; The amount of delay required
DELAY: NOP ; 3 cycles
NOP ; 3 cycles
LOOP DELAY; 17 or 5
LOOP instruction occupies 17 clock cycles when condition is true and 5 clock cycles otherwise. Condition will be true 'N' number of times and false just once when control comes out of loop.
To calculate 'N':
Total clock cycles = clock cycles for MOV + N (2*NOP clock cycles + 17) - 12 (when CX = 0)
5000 = 4 + N (6 + 17) - 12
N = 5000/23 = 218 = 0DAh
So the counter CX must be initialized by 0DAh in order to get delay of 1 millisecond.