Binary Search Tree let three types of traversals by its nodes. They are:
- Pre Order Traversal
- In Order Traversal
- Post Order Traversal
In Pre Order Traversal, we carry out the following three operations:
- Visit the node
- Traverse the left subtree in preorder
- Traverse the right subtree in preorder
In Order Traversal, we carry out the given three operations:
a) Traverse the left subtree in inorder
b) Visit the root
c) Traverse the right subtree in inorder.
In Post Order Traversal, we carry out the three operations which are following:
a. Traverse the left subtree in postorder
b. Traverse the right subtree in postorder
c. Visit the root
Assume the BST of Figure
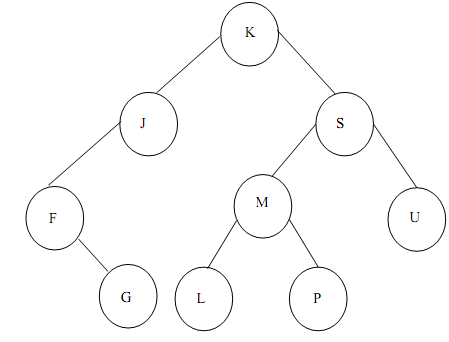
Figure: A Binary Search Tree(BST)
The given are the results of traversing the BST of Figure:
Preorder : K J F G S M L P U
Inorder : F G J K L M P S U
Postorder: G F J L P M U S K