To relieve some programming burden, project 5 is a group project that two students can form a group to do and submit one report. In your submitted report, please specify who is your partner. Of course, you can do this project alone if you want to or have hard time to find a partner.
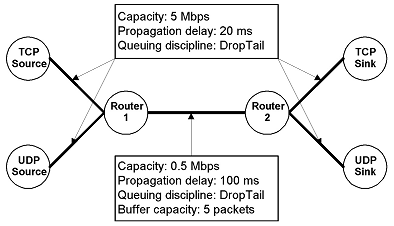
You are required to create the above topology and specified links (don't consider the buffer capacity requirement). Both of the TCP and UDP sources should start transmitting at time 0.01 second, and stop at time 4.0 seconds. Configure the UDP source to be a CBR source, sending packets of size 1000 bytes, at a rate of 0.2Mbps. Configure the UDP sink to be a NULL sink. TCP source is a FTP source. Then add loss model to the link between two routers (see Page 41 in our ns2 lecture notes). Use the following to define the error model:
set loss_module [new ErrorModel]
$loss_module set rate_ 0.02
$loss_module unit pkt
$loss_module ranvar [new RandomVariable/Uniform]
$loss_module drop-target [new Agent/Null]
To make it consistent among all students, make sure that the TCP source node has node ID 0, UDP source node is ID 1, Router 1 is ID 2, Router 2 is ID 3, TCP sink node is ID 4 and UDP sink node is ID 5.
Run the simulation, and then based on the output trace file (give the file name as "out.tr"), you need to answer:
1). How many packets are generated by TCP source and UDP source, respectively? How many ACK packets are generated by the TCP sink?
2). On the link between two routers: How many TCP data packets being dropped? How many TCP ACK packets being dropped? How many UDP packets being dropped?
3). What is the average throughput on the link between two routers during the 4 seconds simulation time for the TCP data traffic and the UDP traffic, respectively? The throughput is defined as the bytes received by the router #2 divided by the time interval.
Submission: Please submit your report document (a word file or PDF file), your simulation tcl code, and your output trace file "out.tr", and your analysis code if you program one. If you use "grep" or other Unix commands for data processing, please give the commands you have used in your report.