TCP/IP protocols are managed into five basic layers. Although some layers of the TCP/IP reference model related to layers of the ISO reference model, the ISO layers procedure does not have a layer that corresponds to TCP/IP Internet Layer.
TCP/IP reference model is given in the figure below.
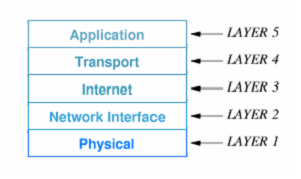
LAYER 1:
Corresponds to physical network hardware layer in OSI.
LAYER 2:
Specifies how to manage data in frames.
LAYER 3:
Specifies the format of data packets transmit across an Internet and forwards data packets.
LAYER 4:
Specifies how to ensure reliable communication.
LAYER 5:
Like 6 and 7 in OSI architecture, it specifies how one application needs an Internet.
HOST COMPUTERS, ROUTERS AND PROTOCOL LAYERS:
TCP/IP describe the term host computer to refer to any computer machine that connects to an Internet and executes applications. A TCP/IP protocol makes it worth full for any pair of hosts to interact despite hardware differences.
Both routers and host require TCP/IP protocol software but routers do not require layer 5 protocols for applications, as they do not execute applications.