Hyper Cube
A Hypercube interconnection network is increament of cube network. Hypercube interconnection network for n ≥ 3, can be distinct recursively as follow:
For n = 3, it cube network in which nodes are allocted number 0, 1, ......,7 in binary. In other words, one of the nodes is allocated a label 000, another one as 001.... And the final node as 111.
Then one node can communicate with one other node if their labels vary in exactly one place, e.g., the node with label 101 might communicate directly with 001, 000 and 111.
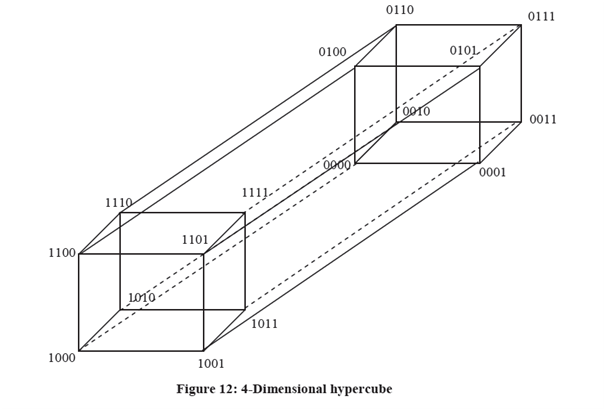
For n > 3, a hypercube can be described recursively as follows:
Take two hypercubes of dimension (n - 1) each having (n -1) bits labels as 00....0,
......11.....1
Next join the two nodes having similar labels each (n - 1) -dimension hypercubes and connect these nodes. Next prefix „1? the labels of one of the (n - 1) dimensional hypercube and „0? to the labels of the other hypercube. This entire the structure of n-dimensional hypercube. Direct connection is only among that pair of nodes which has a (solid) line linking the two nodes in the pair.
For n = 4 we draw 4-dimensional hypercube as show in Figure 12: