How does Intranet Work?
An Intranet can be defined as a private network which uses Internet tools. The principal tool is the Web browser, but there are other Internet tools such as ftp and telnet that are useful. The resources defined as private maybe protected physically (with a firewall or a separate physical network), geographically (by restricting access to computers with a network address on the local network), or personally (by username and password).
Typically, resources will be private either because they are confidential to the organisation (for example, an internal telephone directory), or because they are covered by restrictive licenses (for example, if the Library subscribes to a bibliography whose license restricts tissue to members of the University).
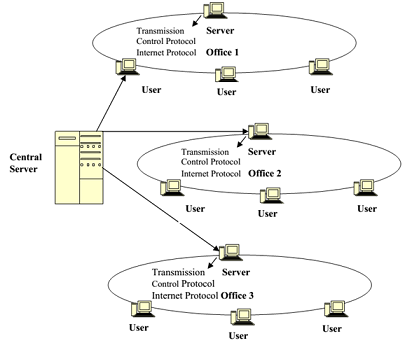
For an Intranet to work, all computers connected together in a network (as shown in Figure) must speak and understand the same language, or protocol. The language used is Hyper Text Mark-up Language (HTML) and the protocol that both Intranets and the Internet use are called Transmission Control Protocol/Internet Protocol or TCP/IP. A network server supports all the activities of an Intranet. On the clients' side, a software, known as a browser, is used. (The browser is usually either Netscape Navigator or Internet Explorer.)
The browser, when invoked, seeks a server computer through the communication medium that has the first page or Home Page of the Intranet, which is usually seen in the folders as 'index.htm'. This is the default page for accessing the Intranet from any computer attached to an internal network. This is what automatically appears on the screen when a user logs in and clicks on the browser icon on the desktop for accessing the Internet also. The hyperlinks to specific files or databases requests for files send the control from anywhere on the network to the browser. The server accesses the file and sends back a copy of what it contains tothe computer or client that has requested for it.
It is the simplicity of TCP/IP that makes Intranets so easy to set-up. Web browsers can be used to connect to virtually any information source, from Structured Query Language (SQL) databases to highly proprietary information systems.