Main Objectives:
• MPLAB In-Circuit Debugger (ICD 2) functionality
• ICD 2 Connection design
• MPLAB ICD 2 setup with the PC and Interface board designed
• I²C Protocol buses technologies
MPLAB In-Circuit Debugger (ICD 2)
The MPLAB ICD 2 debugger/programmer tool: is a low cost real-time debugger and programmer for selected PIC microcontrollers and dsPIC DSCs. The ICD 2 uses two dedicated hardware lines (PGC and PGD) or pins that control In Circuit Serial ProgrammingTM (ICSPTM) of the device and, afterwards, debugging through proprietary, on-chip firmware.
The features of ICD 2 debug are built into the microcontroller and activated by downloading the debug code into the target processor. Some shared overhead expenses are one stack level, general purpose file registers and a small area of program memory when in the debug mode.
The ICD 2 main functions are downloading programs into the microcontroller. The programs are executed in real time and examined in detail with the debug functions of MPLAB. Also set watch variables and breakpoints from symbolic labels in C or assembly source code, and single step through C source lines or into assembly code. MPLAB ICD 2 can also be used as a development programmer for supported MCUs.
ICD2 CONNECTOR
Main Objectives:
- To enable between the ICD2 connector and any suitable peripherals e.g. ICD2 Debugger
- Uploading data or codes into the PIC via the connector
This is a way of plugging a PIC into a standard computer (PC). A separate piece of hardware, called a "Programmer or ICD2 Debugger" is required to connect to one side of the PC I/O port to the PIC on the other side. There are other frequently used connectors such as the parallel port, serial port (COM port), the USB etc.
ICD2 CONNECTOR PIN OUT
Defining the pins of the connectors on an ICD2 cable as shown in Figure below:
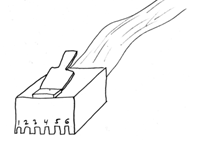
FIGURE: ICD2 cable
The standard In- Circuit Debugger (ICD2) cable is wired so that the pins are flipped between the ends. In other words, pin 1 on one end is connected to pin 6 on the other end, pin 2 to pin 5, etc. The pin out of each end is shown in table 3 below:
Table : ICD 2 PIN OUTS
|
Signal
|
ICD2 end pin
|
Target end pin
|
|
VPP/ MCLR
|
6
|
1
|
|
VDD
|
5
|
2
|
|
GND
|
4
|
3
|
|
PGD
|
3
|
4
|
|
PGC
|
2
|
5
|
|
not connected
|
1
|
6
|