Clos network
This network was organized by Clos (1953). It is a non-blocking network and gives full connectivity like crossbar network but it also requires significantly minimum number of switches. The group of Clos network is shown in Figure :
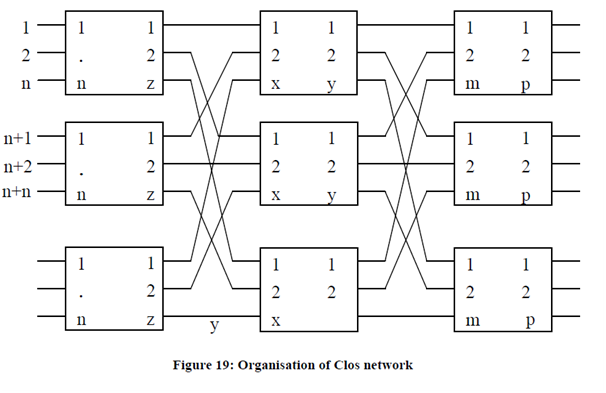
Consider an (I) input and (O) output network
Number N is taken such that (I= n.x) and (O=p.y).
In Clos network input phase will consist of X switches each having n input lines and z output lines. The last phase will consist of Y switches every phase having m input lines and p output lines and the middle phase will consist of z crossbar switches, each of size X × Y. To consume all inputs the value of Z is kept larger than or equal to n and p.
The connection among various phases is made as follows: all outputs of 1st crossbar switch of first phase are connecting with 1st input of all switches of center stage. (i.e., 1st output of primary page with 1st middle phase, 2nd output of primary phase with 1st input of second switch of middle phase and so on...)
The outputs of second switch of first phase. Phases are linked with 2nd input of a variety of switches of second stage (i.e., 1st output of second switch of 1st phase is joined with 2 input of 1st switch of middle phase and 2nd output of 2nd switch of 1st stage is joined with 2nd input of 2nd switch of middle phase and so on...
Like, connections are prepared between center stage and output stage (i.e. outputs of 1st switch of middle phase are connected with 1st input of a variety of switches of third phase.
Permutation matrix of P in the beyond example the matrix entry will be n