Problem a) Give the destination IP address, upper layer protocol, TTL in decimal and header checksum in hexadecimal; the source port number and the destination port number in decimal and hence deduce the application layer protocol this capture is destined to.
00 15 56 3a 4c 79 00 13 02 4a 88 97 08 00 45 00
00 3e 0f 8b 00 00 80 11 a7 90 c0 a8 01 42 c0 a8
01 01 05 61 00 35 00 2a 76 06 f3 5b
Problem b) A UTM graduate has been told to configure a small branch office to provide internal and external network connectivity. The office consists of 6 clients (4 wired and 2 wireless laptops), 1 server with two Ethernet network adapters, 2 network printers, 1 wireless router, one 8-port Ethernet switch and 1 basic ADSL gateway. All the clients will be on dynamic IP addressing and there is need for content filtering on the Internet. Staff are not allowed to access certain external sites e.g. Facebook or download some specific content such as mp3 files.
The layout of the office is given below:
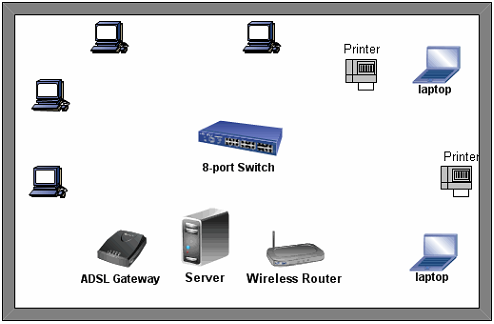
Sketch a suitable physical network diagram for the office bearing in mind sound design principles. Your diagram should show how you would interconnect the devices present. You should mention specific system software you would be required as well as the topology, the network class you will be using. You should describe how you would configure specific services, for example Proxy, DHCP, ... on the server. Additionally, you should give the network configurations of 1 wired PC , 1 laptop, 1 printer, both server NICs and the ADSL gateway.