Reference no: EM131967085
Assignments
Task 1
Assignment: Use Mock Objects to Test Software
As explained in this week's readings, mocks provide a way of unit testing methods that depend upon other methods. Normally, this would be termed "integration testing." But with mock objects, the software tester can isolate the method being tested. Do the following:
• In an object-oriented programming language of your choice, write an application with the following classes and methods. The BitcoinPricer object contains a single public method, which determines the current dollar value for a specified amount of Bitcoin. It uses the BitcoinValueService, which contacts a Web service to obtain the current U.S. Dollar value for a single Bitcoin.
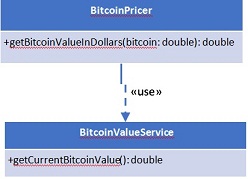
• Write appropriate unit tests for the BitcoinPricer class, ensuring that you have adequate coverage of the possible input space. The tests should appropriately mock a BitcoinValueService object. You should locate, install, and use an appropriate mocking framework for this portion of the assignment.
• Write appropriate integration tests for the BitcoinPricer class. The tests should not mock a BitcoinValueService object and should use the real Bitcoin value at that moment.
• Prepare and submit a Word document with screenshots of all your code, running tests, and test reports.
Task 2:
Assignment: Set Up a Continuous Integration Solution
Research source code control and continuous integration solutions that are appropriate for the program you wrote in Task 1. Set up a continuous integration pipeline that will compile your code, run your tests automatically when code is checked in to source control, and alert you via email when the tests fail. Prepare a Word document with the following components:
• Justification for your selected source control and continuous integration solutions
• Screenshots of your CI solution's configuration showing the triggers and alert settings
• Screenshots of your CI solution's log for a successful check-in and running of tests
• Screenshots of your CI solution's log for a failed check-in due to a syntax error (i.e., inject a syntax error that will cause your app not to compile)
Screenshots of your CI solution's log for a failed check-in due to a logic error (i.e., inject a logic error that will cause your app to compile, but fail one or more tests).