Reference no: EM131210531
Question 1 -
Write a client-server program. The server has the following properties:
- It wait for requests at port 12345.
- It will create a thread to serve one incoming request.
- In each request, an integer is sent from the client. Then, the server will send back the average of all the numbers that have been sent to the server. The average should be of type double.
- Since the server is multithreaded, make sure that your system is thread safe.
- You should also write a client so that the user can send in a number and display the current average.
The client should look like this:
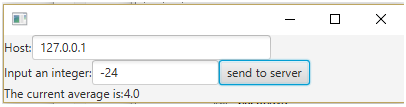
The first text field is used to set the IP address of the server. The second text field is used to input an integer. The connection is created when the button is pressed. The bottom line shows the current average held by the server.
Question 2 -
Rewrite question 1 as a Web service. The client should look the same as that in question 1.
Please note that the host field in the client should have no use as the client is tied to a server when you wrote the client. Therefore the client is not free to choose the server. So in the client, you just ignore the contents in the Host field.
Question 3 -
Rewrite the server of question 1 but use a database to store the information from clients instead of attributes. For example, you may have attributes in your answer to question 1 to store the total sum of integers and number of requests so far. However, in this question, you should use a database to store them.
In your answer, in addition to the Java program code, you should also give the SQL statements to create your database.
You do not need to rewrite the client in Question 1.
|
What is difference between microeconomics vs macroeconomics
: What is the difference between Microeconomics vs. Macroeconomics? Contrast "monetary policy" from "fiscal policy". Recreate and explain the circular flow model (you may use the whiteboard)
|
|
List the pids of parts with the highest cost
: How would your answers to the above two questions change, if at all, if your system did not support indexes with multiple-attribute search keys?
|
|
Good short-term financial strength
: A company has $100,00 in cash, $300,000 in accounts receivable, $50,000 in inventory and a $300,000 office building. Its current liabilities are $250,000. What is the company's current ratio, and does that ratio good short-term financial strength?
|
|
What is the sustainable growth rate of output over time
: Draw the long- run aggregate supply curves for successive long- run equilibriums with a potential growth rate of real GDP at 2.5 to 3.0 percent per year.
|
|
Write a client-server program
: Write a client-server program. The server has the following properties: It wait for requests at port 12345. It will create a thread to serve one incoming request
|
|
Shares of common stock outstanding
: Last year Biff industries had an operating profit of $4,800,000, paid $290,000 in interest expense. The applicable income tax rate for the year was 33%. The company had 415,000 shares of common stock outstanding at the end of last year. What wa..
|
|
What happens to the price level over successive long runs
: Graphically demonstrate how changes in aggregate demand cause inflation or deflation (falling prices) in the short run.
|
|
Explain whether the individual is in the labor force
: In each of the given cases, explain whether the individual is in the labor force, not in the labor force, employed, or unemployed:
|
|
What are the candidate keys for relation g
: Is there ever a good reason to accept something less than 3NF when designing a schema for a relational database? Use this example, if necessary adding further constraints, to illustrate your answer.
|