Reference no: EM131041836
1. Which of the following is the key shaded part?
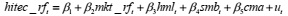
a) 17
b) 24
c) 19
d) 31
e) 33
2. Set of terminal symbol {a, b} and non terminal symbols is {S, A} and starting symbol is S
S → SS
S → aAb
A → aAb
A → b
A → ε
Which strings is not generated by the grammar?
a) ab
b) aabb
c) abab
d) abba
e) ababb
3) What is the decimal value of the sum of the binary number 11001 and hexadecimal number 84 ?
a) 153
b) 154
c) 155
d) 156
e) 157
4) UML diagram
Which of the following possibilities classes A and B be modeled by this diagram?
Class A Class B
a) car Vehicle
b) chapter book
c) country capital city
d) building Floor
e) Judge Lawyer
5)

How many simple paths are there for vertex A to vertex B?
a) 12 c) 45 e) 81
b) 20 d) 64
6) (x, y) Vectors
homogeneous coordinates
Which 3 x3 matrices represent transformation that will mark point (x, y) to point ( x+2, 3 y)?
| a ) |
1 |
0 |
0 |
|
c) |
1 |
2 |
0 |
|
0 |
3 |
1 |
|
|
0 |
1 |
3 |
|
2 |
0 |
1 |
|
|
0 |
0 |
1 |
|
|
|
|
|
|
|
|
|
| b ) |
1 |
0 |
2 |
|
d) |
2 |
0 |
0 |
|
0 |
3 |
0 |
|
|
0 |
1 |
3 |
|
0 |
0 |
1 |
|
|
0 |
0 |
1 |
|
|
|
|
|
|
|
|
|
| e) |
2 |
0 |
1 |
|
|
|
|
|
|
0 |
3 |
1 |
|
|
|
|
|
|
1 |
0 |
1 |
|
|
|
|
|
7) Which of these are not desired characteristics of a hash function in used to construct a hash table?
a) h(x) is an integer value
b) if x = y, then h(x) - h(y)
c) given x, it is easy to computer h(x)
d) given h(x), it is easy to computer x
e) h(x) produces evenly distributed values
8) When value in a programming is said to have first class status if it has which characters?
a) it can be passed as a parameter
b) it can be returned from a function
c) it can be assigned to a variable
this has more than one answer
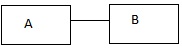
9) Which number when maximum flow from note S to note T?
a) 5
b) 6
c) 7
d) 8
e) 9
10 (aaa + bbb) * (bb +c) *(acb*)(acba*)
Which length of the shortest string in the language represented by the expression?
a) 2
b) 4
c) 5
d) 7
e) 16
11 ) Database management system, an attribute of one table that matches the primary key of another table
a) candidate key
b) composite key
c) foreign key
d) primary key
e) secondary key
12 Quickest algorithm (nlogn)
Which one is the worst case running ?
a) (nlog2n)
b) (n3/2)
c) (n2)
d) (n2logn)
e) (n3)
13 Which binary strings of length 10 contain either exactly one 0 or exactly the 0's?
a) 45
b) 55
c) 100
d) 450
e) 1024
14) "All cold things are wet"
"no blabs are purple"
"same purple things are cold"
Which one of these?
a) some wet things are not blobs
b) some cold things are blabs
c) some blabs are not cold
d) all wet things are purple
e) all purple things are wet
15) Testing to detect the introduction of errors into software that way previously corrected is called?
a) unit testing
b) system testing
c) regression testing
d) integration testing
e) debugging
16 ) Asymptotic ordering from least to greatest of the these functions?
√n, nlog2n, log2(n2)
17) 3 step random walk that starts at node A
The next node will be visited randomly chosen from among two nodes adjacent to the current node.
What is the probability the 3 steps random walk will end at node B?
a) 0
b) 1/8
c) ¼
d) 3/8
e) ½
18. Consider tables R and S
R
S
How many types are in the natural join of R and S?
a) 3
b) 4
c) 5
d) 6
e) 7
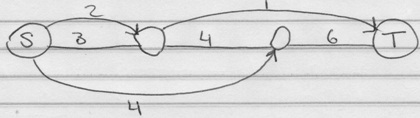
19. An Euler path
This graph is known to have an Euler path because it is planner; all nodes have a degree greater than or equal 2.
Which are of these are true?
a) it has more edges then nodes
b) it has exactly two add degree nodes
c) it has an add number of nodes
There can be more than one answer
20 which of the following two input Boolean function cannot be learned by a single layer neural network such as a perception?
a) AND
b) OR
c) NAND
d) NOR
e) XOR
21) Consider a computer system with 32 bit address, 4 GB of byte addressable RAM, and a data cache that has 32 byte blocks. What additional information can be used to compute the size of a tag in the data cache?
a) The size of the data cache in byte and the number of blocks per ser
b) the number of page table entries and the number of sets in the data cache
c) the size of the data cache in bytes and the size of a page
d) the size of the cache divided by the number of blocks per set
e) the number of translation look aside buffer (TLB) entries and the number of set in the data cache.
22) The computer graphics operation of rotations, translation, and projection can be all be implemented using matrix transformation from linear algebra. For this reason advanced graphics units (GPU) commonly found in today's microcomputer from which class of computer architecture?
a) SISD
b) SIMD
c) MIMD
e) NUMA
I need some help with my computer science assignment. There are 22 computer science questions in multiple choice. You can just circle the write answers or make a list.