Reference no: EM131183972
Assignment
Part A
Question 1
USQCollege uses OSPF as the dynamic routing protocol for its campus network. The network is not connected to any ISP and is isolated from the Internet.
The in-house network administrator insisted that the existing authentication process for OSPF is not efficient. So he assigned you to re-programmed OSPF such that the authentication process will apply MD5 to a message and the output will be sent to destination as cipher text. The receiver will apply MD5 and get back the original message.
The network administrator knows that AES is one of the best encryption algorithms we can use. As the next phase of improving the security, he planned to switch from MD5 to AES for OSPF authentication. You are assigned to be in charge of this switching over as your next task.
a) Will you accept the first task or reject it? Explain your reasons for accepting or rejecting the task.
b) Will you accept the second task or reject it? Explain your reasons for accepting or rejecting the task.
c) The network administrator is planning ahead to connect the campus network to an ISP. Assume that the OSPF to be used is the standard version, not the modified version. List and explain the routes to be installed in the boundary router and the ISP router.
d) Assuming the ISP router has an IPv4 address of 200.200.200.1 and the LAN gateway router has an IPv4 address of 201.201.201.1. List the required Cisco commands to install the routes.
e) How can the route to the ISP be transferred to other routers within the campus LAN?
Question 2
Floor plan of the Wolfgang Concern Hall:
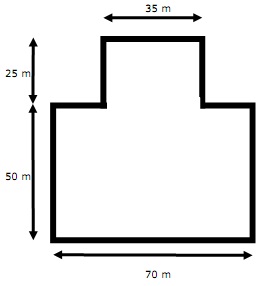
You are going to implement a wireless network to the Wolfgang Concern Hall using access points with an effective range of 14 meters.
a) What is the minimum number of access point do you need?
b) Show
• In a diagram, show how the concern hall was covered by the wireless range of access points. The diagram should also show the coverage of individual access points.
• Your calculation,
• The data you use for the calculation, and
• Any assumptions you made.
c) Which type of access point (independent, controller based, cluster, cloud) will you use? Explain the reason for your choice.
Question 3
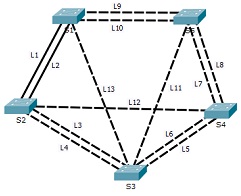
Download Q3.pkt.
Q3.pkt simulates the switched network of ANZCollege. Assume all links are of the same cost.
The top two switches are S1 and S5.
a) Why STP allows links L1 and L2 both to be active?
b) Which switch is the root switch?
c) What is the path assigned by STP:
1. From S4 to root switch?
• Explain why other paths are blocked.
• List the root port(s), designated ports and non-designated ports along the path from S4 to root switch.
2. From S5 to root switch?
• Explain why other paths are blocked.
• List the root port(s), designated ports and non-designated ports along the path from S4 to root switch.
d) Explain the port status for the ports of link L7 and link L8.
Question 4
AUssieCollege uses EIGRP as the dynamic routing protocol for its campus network. The network is connected to an ISP using a single router R1.
a) The in-house network administrator is not happy when R1 fails, all users will be disconnected from the Internet. What would you suggest to improve the situation? Justify your suggestion.
b) The AussieCollege LAN uses Cisco switches and is running STP. What would suggest to improve the convergence speed of the LAN network? Justify your suggestion.
c) The network administrator assigns you to implement redundancy for the network. Provide an implementation plan with supporting reasons to the network administrator.
Attachment:- Q3.pkt