Reference no: EM13835708
Question:
1.Use the template provided in the assignment to write your answers.
2.You should upload the completed template file and the .pcap file
Question 1:
Given the following network, construct the routing table of router R1:
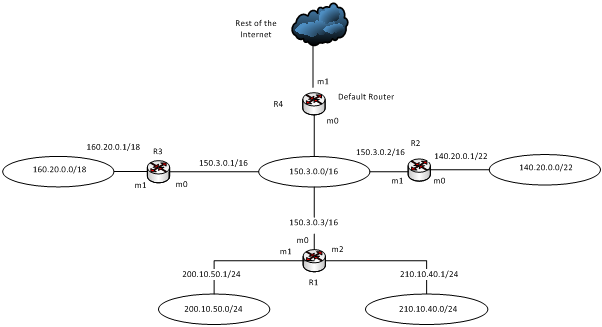
Question 2:
An organisation has been granted a block of addresses starting with the address 172.154.60.0/24.
a) Create 4 subnets for this organisation with the first subblock of 120 addresses, the second subblock of 60 addresses,the third subblock of 30 addresses and the fourth subblock of 12 addresses. (1 mark for each correct answer)
b) How many addresses are left?
Question 3:
Consider the following UDP header dump:
a) Identify the source port number.
b) Identify the destination port number.
c) What is the length of the data?
d) Is it a packet from the client to the server or vice versa?
e) What is the client process?
Question 4:
Using Wireshark tool capture the packets at the same time that you download Lecture 2 from the COIT20229 Course Webpage. Before you undertake this task, you should have Wireshark installed in your home computer/notebook and connected to the Internet. It is recommended that you undertake the packet capture exercises using Wireshark that are scheduled for Weeks 8-9 before you attempt this question. You may not be able to complete this task in any CQUniversity lab.
a) Submit the captured pcap file. You should filter the file so that only TCP traffic is included. (1 mark). Note: If you do not upload the .pcap file, you will receive zero marks for most parts of this question.
b) What is the server IP address?
c) What is the application layer protocol involved?
d) What is the client port number for data download?
e) What is the server port number for data download?
f) How many data bytes have been downloaded?
g) What is the size of the downloaded Lecture 2 file?
h) Discuss the difference in your answers to parts f) and g). You need to consider the packet formats in your discussion.
Question 5:
Investigate the cloud-managed wireless networks and compile a brief report of around 1400 words. Your references may come from websites, white papers, government documents or published conference or journal papers.
Your report should include only the introduction (about 200 words), body (about 1000 words), conclusion (about 200 words) and the reference list (Do not include the executive summary and table of contents). Use the sub-headings given in the template and include in-text references in the body of the report. Use Harvard style of referencing for the list of references and in-text references.
Marks allocation:
1. Introduction.
2. Architecture.
3. Advantages and disadvantages.
4. Key service providers.
5. Any other relevant information.
Conclusion:
A well written coherent conclusion
References:
Adhered to Harvard reference style
Question 6:
Given the following IPv6 addresses in hexadecimal colon notation, answer the following questions. Where applicable provide your answers in fully expanded hexadecimal colon notation.
a) What is the full (expanded) address of the abbreviated IPv6 address FDEC::CF:0:FFFF?
b) What is the type of block of the abbreviated IPv6 address
2001:A100:FC1::A4B8:AE12:3217:FCBA?
c) What is the type of address of the abbreviated IPv6 address 0::FFFF:194.42.12.7?