Reference no: EM135112
The purpose of this program is to change such that it makes use of the IPC facilities provided by UNIX.
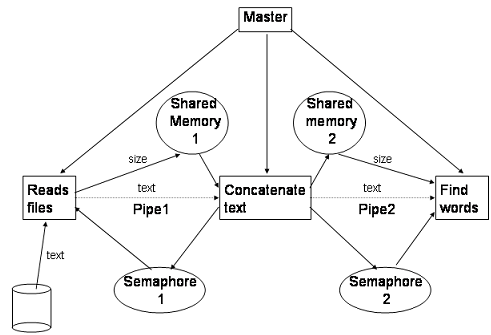
Master:
• Accepts command line inputs (N filenames and string to find).
• Forks "Reads Files,"(repeatedly, once for each input file) "Concatenate Text," and "Finds word."
Reads Files:
• Accepts command line inputs (1 filename, 1 pipe ID, 1 semaphore key, and 1 shared memory key).
• Reads text from the specified file and determines how big the file is.
• Creates a dynamic 1D array to hold the text.
• Strips repeating blanks from the text.
• Determines the resulting size of the text.
• Writes the new size into shared memory 1.
• Waits for semaphore 1to be set (by Concatenate Text program).
• Writes the text into pipe 1.
• Terminates.
NOTE -To terminate the entire process you can assume that the filename "EXIT" will be sent to this program. You can use this to set shared memory 1 to -1.
Concatenate Text:
• Accepts command line inputs (2 pipe IDs, 2 semaphore keys, and 2 shared memory keys).
• Waits for a non-zero value to be written into shared memory 1.
• Creates a dynamic 1D array large enough to concatenate the new text with any old text.
• Copies the old text into the new array.
• Sets semaphore 1.
• Set shared memory 1 to 0.
• Reads data from pipe 1.
• Concatenates the new data with the old.
• Waits for next data stream (non-zero in shared memory 1).
NOTE -If this program finds a -1 in shared memory 1 it will assume that all of the data to be concatenated has been sent. At this point this program will:
o Write the final text size into shared memory 2.
o Waits for semaphore 2 to be set (by Find Words).
o Writes resulting text into pipe 2.
o Terminates.
Find Words:
• Accepts command line inputs (1 pipe ID, 1 semaphore key, 1 shared memory key, and 1 string to find).
• Waits for a non-zero value to be written into shared memory 2.
• Creates a dynamic 2D array of characters (80xM) large enough to hold the combined text.
• Sets semaphore 2.
• Reads text from pipe 2.
• Searches for the text passed in by:
o Scans the 2D array (crossword like manner -by rows, by column, by diagonal) looking for the string.
o If the string is found, continue scanning the text in the same "direction"to find the secret message. Your program must print out this secret message.
• Terminates.
|
What is the focal length of lens
: A contact lens is made of plastic with an index of refraction of 1.36. The lens has an outer radius of curvature of +1.91 cm and an inner radius of curvature of +2.41 cm. What is the focal length of lens?
|
|
What is the wavelength of the incident beam
: A monochromatic beam of light is absorbed by a collection of ground-state hydrogen atoms in such a way that three different wave-lengths are observed while the hydrogen relaxes back to the ground state. What is the wavelength of the incident beam.
|
|
Describe the competitive strategies used by competitors
: Describe the competitive strategies used by each of William-Sonoma's competitors. Which of these strategies are the most effective
|
|
What is the temperature of the ocean water
: Assuming the diver has inhaled a negligible amount of air from the tank, what is the temperature of the ocean water.
|
|
Use of the ipc facilities provided by unix
: The purpose of this program is to change such that it makes use of the IPC facilities provided by UNIX.
|
|
Find the magnitude of the horizontal component of the plane
: A jetliner is moving at a speed of 187 m/s. The vertical component of the plane's velocity is 44.5 m/s. find out the magnitude of the horizontal component of the plane's velocity.
|
|
What is the normal force on it because of bottom of the bowl
: The work completed by friction on the rock when it moves from point to point at the bottom of the bowl has magnitude 0.22. Just as the rock reaches point, what is the normal force on it because of the bottom of the bowl .
|
|
What is the exposure rate
: A current of 10^-14 A is produced in a free-air chamber operating under saturation conditions. The sensitive volume, in which electronic equilibrium exists, contains 0.22g of air. What is the exposure rate .
|
|
Explain sales incentive program
: Her company International Widgets implements a sales incentive program- If any salesperson sells 100 units in July, they will receive a $12,000.00 bonus. International states that the program is discretionary and that International may change it a..
|