Reference no: EM131310347
1. Visit cysecure.org and download the file LinuxDistributors.txt.
a. If you can copy the content directly and paste onto your linux file, or
b. Download it first into your computer. Then, copy and paste it from your computer to you linux file.
2. From the file download as above, produce a new file which contains the first and second fields, plus the fourth to the sixth fields. So, the files contains the following:
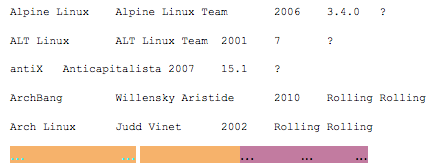
Note that fields 1 and 2 are on the left and followed by the fields 4, 5 and 6 on each row.
3. Do the excise on pages 229 -231 by changing a little as follows:
a. Generate 1000 phone numbers
b. Find out all the phone numbers, (9xx) 5xx-xxxx.
c. Submit, the regular expression used successfully for 03.b above.
https://www.youtube.com/watch?v=fZfrHJhgNIg&feature=youtu.be
https://www.youtube.com/watch?v=k7E5k3KCLPU&feature=youtu.be
In this assignment submit Screenshots of your program execution. The file produced as guided above and Regular Expression for Q3.c.
|
Describe bottoms adventure with titania
: Describe Walter Lee's conflict and general state of mind throughout most of the play.Describe the value system that prevailed in Helmer's household. What demand did Nora ultimately make?
|
|
How performance cycle variance can be controlled
: Discuss uncertainty as it relates to the overall logistical performance cycle. Discuss and illustrate how performance cycle variance can be controlled.
|
|
Create a class named order that performs order processing
: Create a class named Order that performs order processing of a single item. Create a subclass named ShippedOrder that overrides computePrice() by adding a shipping and handling charge of $4.00.
|
|
Differences between transactional and relationship marketing
: Explain the differences between transactional and relationship marketing. How do these differences lead to increasing emphasis on logistical performance in supply chain management?
|
|
Produce new file which contains the first and second fields
: From the file download as above, produce a new file which contains the first and second fields, plus the fourth to the sixth fields. So, the files contains the following: Note that fields 1 and 2 are on the left and followed by the fields 4, 5 and ..
|
|
Will the firm need external funds
: Using the percent of sales method, forecast the new balance sheet for sales of $600,000 assuming that cash changes with sales and that the firm is not operating at capacity. Will the firm need external; funds?
|
|
How can a company attempt to eliminate the knowledge gap
: Which of the gaps in Figure do you think represents the major problem for most firms? How can a company attempt to eliminate the knowledge gap? The communications gap?
|
|
Read the threads of your classmates and the articles
: Read the threads of your classmates and the articles which are referenced (this is why it is imperative that the articles be accessible via working URL links). Expect to spend some time each day reviewing all threads and replies, even those in whi..
|
|
Modify a classical cryptosystem to provide nonrepudiation
: The ciphertext corresponds to the plaintext enciphered under the secret key that Alice and Bob share. Explain why this does not satisfy the requirements of nonrepudiation of origin. How might you modify a classical cryptosystem to provide nonrepud..
|