Reference no: EM131144845 , Length:
Question:
The output of the commands has to be captured and write some information about command in an word file.Project 2 - Part 1 Process Management
In a new Linux virtual machine within VMPlayer:
1. To obtain process information for the UNIX or Linux system, use the command ps-ael. Use the command man ps to get more information about the ps command. Describe what this command does.
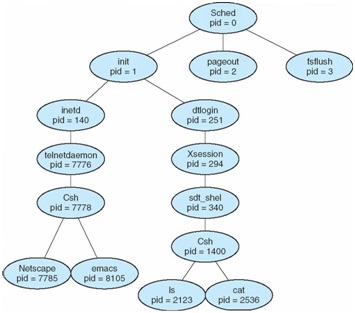
2. Construct a process tree similar to Figure 1. Look up the Linux command pstree -p and describe what it does. Then type in the command the capture the output.
3. Create a process in the background ( such as (date;sleep 10; date) >date.out & ), and run ps -ael and identify the added processes running now.
4. Verify the job is running by typing the command jobs. Describe what this command does.
5. Type the following program in a textfile called three_forks.c. Compile it using gcc and then run it in the background.
a) Describe what the fork() call does.
b) Including the initial parent process, how many processes are created by the program shown? Verify your answer by running ps -ael.
c) Kill the processes created in this part one by one and terminate them by the kill command. Show each is killed by running ps -ael.
Tasks
1. Create a user called "victim" with sudo privileges and create a directory called "public" for him with rwx access for all.
2. Create a user called "attacker" with no sudo privileges. Log in as this user and create a malware file called "date" to mascaraed the date Linux command. This malware file should give sudo privileges to attacker.
3. Run a scenario in a Linux bash shell to demonstrate and verify that after the scenario is executed, attacker is given sudo rights by victim. Test actually that attacker has sudo privileges now.
Capture all the key screens using a screen capture tool (such as Windows 8) snipping tool. Put all captures in you MS Word project report file with some explanation of what each major step is.
Answer the following questions:
1. If after giving himself sudo privileges, attacker wanted to change victim's password, what commands should type in Linux?
2. Look up what bashrc file is and in one paragraph describe it.
#include <stdio.h>
#include <unistd.h>
// Note that fork() returns a pid - it returns a 0 to the child process...
int main()
pid_t mypid, pid;
printf("Start: pid = %d\n", getpid());
/* fork a child process */ pid fork();
if (pid = 0)
printf("Child -
else
printf("Parent - ");
printf("After 1st fork: pid = %d\n", getpid());
/* fork another child process */
pid = fork();
if (pid = 0)
printf("Child - ");
else
printf("Parent - ");
printf("After 2nd fork: pid = %d\n", getpid());
/* and fork another */ pid = fork();
if (pid = 0)
printf("Child - ");
else
printf("Parent - ");
printf("After 3rd fork: pid = %d\n", getpid());
while ( );
return;
The output of the commands has to be captured and write some information about command in an word file
|
Prepare a schedule of cost of goods manufactured
: During the month, the company purchased $164,000 of raw material; direct material used during the period amounted to $128,000. Factory payroll costs for July were $197,000 of which 85 percent was related to direct labor. Overhead charges for deprecia..
|
|
Prepare a work breakdown structure
: prepare a Work Breakdown Structure, a Gant Chart with the critical path and a Project Team Org Chart with contact information.
|
|
Summarize three of most important messages of iom reports
: From your perspective as a health care professional and/or consumer, summarize two or three of the most important messages of the IOM reports To Err is Human and Crossing the Quality Chasm.
|
|
Discuss both the financial and nonfinancial factors
: Determine the net credit and collection expense in dollars and as a percentage of sales after considering the revenue not earned from other investment opportunities.
|
|
Obtain process information for the unix or linux system
: Create a process in the background ( such as (date;sleep 10; date) >date.out & ), and run ps -ael and identify the added processes running now.
|
|
Explain why it would be the appropriate technique to apply
: Provide at least one example of when you might use (1) the minimal-spanning-tree technique, (2) the shortest path, and (3) the maximal flow through a network technique. and explain why it would be the appropriate technique to apply in each of the ..
|
|
What types of modifications to the model would eliminate
: Why does the varieties model of technological change from section 6.1 exhibit a scale effect in the sense that the growth rate rises with the aggregate quantity of labor, L? Is it reasonable to identify L empirically with a country's population?
|
|
Identify one of the six dimensions of quality
: Identify one of the six dimensions of quality (safety, effectiveness, patient-centeredness, timeliness, efficiency, or equity) that you would like to focus on for this Discussion.
|
|
What are some of the benefits of factoring
: If a company factors its receivables, what percentage of the value of the receivables can it expect to receive from the factor in the form of cash, and how quickly will it receive the cash?
|